
Introduction
Digitisation is all around us, and it is happening so quickly that it takes time for us to be adapted to the changes. There are numerous concerns and risks associated with the digitisation process, but one of the most serious is referred to as a threat to privacy in the digital age. Invasion of privacy is becoming a major concern by the minute, and though there are numerous security options available, the increased popularity of social media networks has made people vulnerable. Because a great deal of personal information and data are being shared, it is now vulnerable of people to encounter a variety of global threats. In the last decade, governments, as well as large corporations such as Facebook and others, have become data miners, collecting information on people’s activities, behaviours, and lifestyles. This extensive data collection has given rise to the cynical belief that privacy has died (Bloustein, 2018).
The digital age has brought many risks to people in the 21st century, with the threat to privacy being the most concerning.
Statistics about privacy and cyber attacks
People around the world have widespread concerns about their privacy in the digital world. According to research conducted in the United States, approximately 79% of people are concerned about their online privacy as a result of companies infringing. Around two-thirds of respondents said they don’t trust their government when it comes to privacy and the Internet surveillance. The majority of people believe that data is less secure now, and that data collection by companies poses more risks than potential benefits. Six out of ten respondents stated that it is practically impossible for them to go about their daily lives without having their data collected by companies. When the government is involved in the process, an increasing number of 81% of respondents in the survey said they have a lack of control over the data that is collected by companies, while the same phenomenon was endorsed by 84%. In the case of companies, the risk outweighs the potential benefits by 81%, while for governments, the risk outweighs the potential benefits by 66%. Concerns about data usage have been expressed by 79% of respondents from the companies, and 64% from the government (Pew, 2019). As a result, these statistics provide a clear picture of people’s lack of trust in their respective governments and companies to collect data and use it for positive purposes, even in the developed world. Therefore, this creates a more comprehensive threat to privacy that must be dealt with effectively.
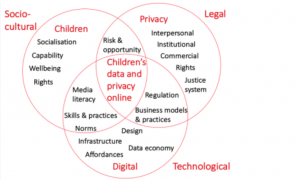
Figure 1: Children’s Data and Privacy Online (Livingstone et al, 2019)
In the 21st century, cybersecurity has become a difficult aspect of data privacy and security. According to Microsoft’s research, identity theft related to cyber was 42% in 2020, and the healthcare sector was the most targeted industry, with data breaches costing it around $6 trillion in 2020 (Wylde et al, 2022). Cognyte is a cybersecurity analytics firm that witnessed a major database breach in 2021, resulting in a 5 billion record breach in May. LinkedIn’s data breach in June-August 2021 also exposed 700 million records. Facebook, a social media giant, also suffers a breach that exposes the data of 533 million accounts. In January 2021, the Brazilian Ministry of Health also lost 223 million records (Jhanjhi et al, 2021). According to an IBM 2020 report, the most targeted industries are finance and insurance, manufacturing, energy, and retailing. So, the issue of privacy is not a myth; rather, it is founded on facts provided by governments and authenticated sources on a global scale. Even giants like Facebook and many other major businesses are vulnerable to hackers’ attacks, which is why it is critical to discuss the privacy issue in the digital issue and propose appropriate measures to achieve the desired results in a structured manner.
Privacy regarding challenges in Digital Age
The user’s personal computer interacts with the Internet by utilising the various environments that are grouped under the social networking sites. It is a useful tool that connects the user to information. However, it is possible that sharing information with an unauthorised person can have negative psychological as well as financial consequences. During the first visit, a website frequently serves as an open door, and users frequently accept the privacy policy with a single click instead of careful reading it (Wasastjerna, 2018). As a result, you accept all conditions without even realising it. Therefore, there is a significant risk to an individual’s privacy and data because he or she has no control over the personal data that exists on the website during the profile creation process. Another issue in this regard is the transfer of data to the centre without the user’s awareness or consent. According to the research in this area, only 54% of social network users are aware of the conditions that exist when collecting personal data. In some cases, the media does not provide information about privacy policies or asks too many questions, which violates GDPR principles of personal data violation. Global networks are frequently used for the storage of personal data, which leads to hackers’ attacks and an increase in the threat to users’ privacy (Romansky et al, 2020).
Cloud computing entails connecting virtual computers via a dynamic communication structure to provide cloud services to users in the most structured manner. NIST, IaaS, PaaS, and SaaS are the fundamental cloud services. These cloud services are delivered through a variety of arrangements, including public, private, community, and hybrid. According to the Thales 2020 report, approximately 83% of corporate entities use eleven or more SaaS providers to obtain structured services. It is also stated that approximately 48% of corporate data in the cloud is of a much more sensitive nature. Only 57% of such data is encrypted, leaving room for hackers to attack and steal it for malicious purposes (Lee et al, 2020). Cloud computing does not violate any privacy or data protection principles, but there is a risk of cross-border data transfer in this regard.
Internet of Things (IoT)
IoT is defined as a collection of devices that communicate with one another via the Internet. There is an increased risk that these devices will disrupt privacy and security while undermining consumer confidence. Because of the increased number of sensors used in the process of data accuracy, there is a strong link between the lack of confidentiality and security in the phenomenon of IoT. One example is hacking smart sensors, which results in access to collected data that can be useful for such individuals to learn about certain habits and religious data. Traditional passwords are used by various computers and internet devices that can be the targets of various attacks (Duarte, 2016). These attacks are primarily directed to computers with a low level of cyber hygiene, making it easy for hackers to identify potential vulnerabilities and tempering. Identification verification is also a major privacy concern because it does not provide the necessary level of access control. Several studies have found that IoT devices are vulnerable to cyberattacks. Therefore, consumers are concerned about their privacy and the deprivation of individual rights, as well as third-party access to sensitive and confidential information.
Big Data & Analytics
Big data is based on collecting and storing a large volume of information from various sources for further processing for a variety of reasons. The idea is that more data is better, but in the long run, it poses a threat to privacy. Big data itself does not pose a threat to an individual’s privacy or security, but it can lead to a negative effect. Certain characteristics are linked to unfavourable privacy consequences. It violates data minimisation principles, which are prominent principles of GDPR (Trautman, 2018). Incorrect data interpretation can also create difficulties for individuals, which can lead to problems in the long run. There is evidence of incorrect conclusions in business marketing research using big data, which can jeopardise individuals’ reputations as well as the accuracy factor, which is also alarming in this context.
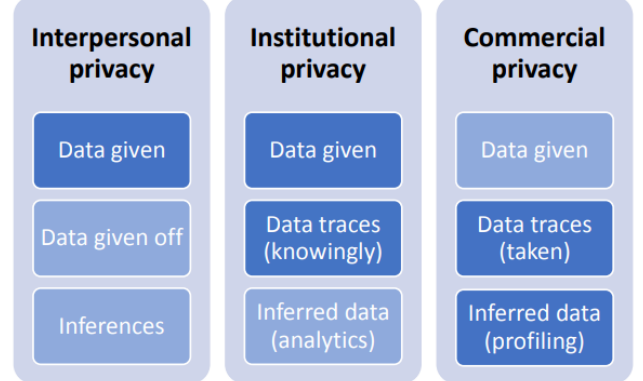
Figure 2: Dimensions of Privacy (Livingstone et al, 2019)
Facebook as a Case Study
It is important to note that social media platforms, such as Facebook, make rules that are beneficial to their commercial interests. That is why, in 2009, Facebook’s owner reneged on its commitment to making the platform more democratic (Suzor, 2019). Terms of service designed by the company protect the legal interests of the company rather than the customers, posing a significant threat to the privacy of its members. In the case of social media platforms such as Facebook, there is no such thing as neutral because they make the rules that suit their interests. Celeste Liddle’s Facebook account was suspended in 2006 after she posted images of topless desert women dressed up for a ceremony performing a traditional dance. Her speech emphasised the double standards of the modern western culture. This raises an important question that it is not the people who make the rules, but the corporations who allow the people to express their opinions. Facebook has paid a $550 million privacy lawsuit that claimed the company violated an Illinois state law that requires companies to obtain information from users in order to save their biometric data (Ayaburi et al, 2020). There is a long history of data breaches on this platform, which makes people concerned about their privacy and data misuse, and despite all of these problematic situations, the company is still working to make it safe for customers. It was also revealed that in March 2018, Cambridge Analytical, a political consulting firm, accessed the data of approximately 87 million US Facebook users and later sold it to third parties, including Donald Trump, for his 2016 election campaign (Flew, 2018). It was the 15th time the company was questioned about the use of personal data and raised serious concerns about the privacy of people using social media networks. So, regardless of the size of the organisation or domain, privacy is under threat, which is why awareness and education in this regard is the ultimate solution that should be implemented in a meaningful way.
Conclusion
The digital age has facilitated every sector, but one major risk in this regard is the threat to people’s privacy. Facebook is one prominent example, as data was breached numerous times and even used without the customer’s consent, resulting in lawsuits and settlements in the end. As a result, customers must understand the privacy implications of Internet-based instructions and take appropriate precautions. However, in a broader sense, it is the role of governments and businesses that must be monitored legally in a structured manner. Every Internet user’s privacy will be properly secured in this way, and no one will think they are being watched.
References
Americans and Privacy: Concerned, Confused and Feeling Lack of Control Over Their Personal Information. (2019). Retrieved 30 March 2022, from https://www.pewresearch.org/internet/2019/11/15/americans-and-privacy-concerned-confused-and-feeling-lack-of-control-over-their-personal-information/
Ayaburi, E. W., & Treku, D. N. (2020). Effect of penitence on social media trust and privacy concerns: The case of Facebook. International Journal of Information Management, 50, 171-181.
Bloustein, E. J. (2018). Individual & group privacy. Routledge.
Duarte, R. P. G. M. (2020). Case Study: Facebook in face of crisis (Doctoral dissertation).
Flew, T. (2018). Platforms on trial. Intermedia, 46(2), 24-29.
Jhanjhi, N. Z., Humayun, M., & Almuayqil, S. N. (2021). Cyber Security and Privacy Issues in Industrial Internet of Things. Comput. Syst. Sci. Eng., 37(3), 361-380.
Lee, S. M., & Lee, D. (2020). “Untact”: a new customer service strategy in the digital age. Service Business, 14(1), 1-22.
Livingstone, S., Stoilova, M., & Nandagiri, R. (2019). Children’s data and privacy online: growing up in a digital age: an evidence review.
Romansky, R. P., & Noninska, I. S. (2020). Challenges of the digital age for privacy and personal data protection. Mathematical Biosciences and Engineering, 17(5), 5288-5303.
Suzor, N. P. (2019). Lawless: The secret rules that govern our digital lives. Cambridge University Press.
Trautman, L. J. (2018). How Google Perceives Customer Privacy, Cyber, E-commerce, Political and Regulatory Compliance Risks. Wm. & Mary Bus. L. Rev., 10, 1.
Wasastjerna, M. C. (2018). The role of big data and digital privacy in merger review. European Competition Journal, 14(2-3), 417-444.
Wylde, V., Rawindaran, N., Lawrence, J., Balasubramanian, R., Prakash, E., Jayal, A., … & Platts, J. (2022). Cybersecurity, Data Privacy and Blockchain: A Review. SN Computer Science, 3(2), 1-12.