
With the advent of the new media era, the development and application of network information technology have brought great convenience to society. Online social media has accelerated the exchange and dissemination of information and has played a positive role in promoting socio-economic, cultural, and many other aspects. However, the destruction of online privacy has become a concern and a nuisance for the whole society and privacy issues related to social media are constantly being discussed.
Westin put forward the concept of “information privacy” for a long time, which he saw as the ability of an individual, organization, or institution to determine when, how, and to what extent private information should be disseminated (1968). The term “information privacy concerns” was introduced by Smith H. J. in 1996 and refers to the inherent concerns arising from the potential loss of information privacy (Smith et al., 1996). This concept has been widely used in research related to e-commerce and social media contexts. The digital means of access, processing, and dissemination have made personal information increasingly transparent and invisible. In addition, the network economy is highly profit-driven due to the lack of unified and standardized management and constraints on network privacy. The awareness of personal privacy protection is weak. People gradually and generally feel the threat of privacy leakage.
This blog will take the privacy leakage in the use of social media WeChat as an example, analyze the privacy threats of social media in the digital age, and make some suggestions on how to protect the security of private information effectively.
Personal privacy information leakage problems in WeChat use
In recent years, the rapid development of social media has brought an increasingly significant impact on people’s lives. WeChat, According to the “49th Statistical Report on the Development Status of China’s Internet” released by CNNIC, the social networking software with the most significant number of users in China, has become the social media platform with the highest usage rate of Chinese netizens due to its diverse communication forms and unique communication characteristics. WeChat carries a large amount of personal privacy information. WeChat has become an indispensable social tool in people’s lives. However, while WeChat provides excellent convenience to people’s lives, it also faces problems with privacy protection. Some of the functions of WeChat leak users’ privacy information, and there are also privacy infringements caused by users’ self-disclosure of information in WeChat use.
Information leakage caused by WeChat functions: privacy violation by location-based services
WeChat programs “Nearby,” “Shake,” “Moments,” and others that distribute location-based content can involve location-based services that infringe on privacy. Using the” Nearby” program, users can see information about people’s data in the vicinity, and the exact distance of the person from your location is clearly displayed. Although this kind of technical location service to obtain private area means is voluntarily received by others, whether the background voluntarily receives it is open to discussion. In addition, although the “shake” program looks for people who shake their phones at the same time, the information it presents still includes the location of the other person. This is even exposed by default and is an indirect way for WeChat to use external software to obtain the location information of users.
In fact, there are many WeChat users who like to locate their positions in real time and share their lives with others. However, there is a great risk of being stolen and tracked. According to China Daily.com, the function of allowing users to locate distances in WeChat has led to several criminal offenses in China, including rape.
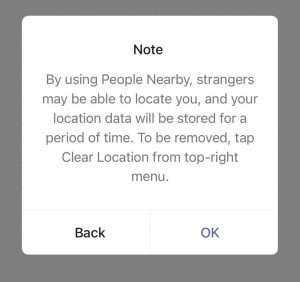
Image. Screenshot from WeChat
Unintentional privacy leakage during user use
According to Nissenbaum’s contextual integrity theory (2009), combined with the public psychology of WeChat use, it can be concluded that posting information on Moments is a way to share life with more people in the hope of building more friendships and gaining more relationship recognition. This kind of public information among friends can be considered a voluntary disclosure, which is not sensitive content involving privacy. However, such behaviors may lead to possible misuse of personal data and property theft by others for other reasons. For example, if a friend takes a screenshot of the contents of their Moment and distributes it to an unknown third party without consent in this field, involuntary content may be involved in the violation of privacy.
In addition, there are also unintentional privacy disclosures by users. Norberg, Horne, & Horne claim a contradiction between the privacy attitudes exhibited by users and their actual privacy disclosure behavior concerning the social life conducted in the form of the Internet (2007). This affirms that the misalignment between “awareness” and “behavior” is joint in the Internet state. Middle-aged and elderly users lack the correct concept of controlling privacy boundaries. False advertisements or unknown links attract them, so they click to browse and easily disclose their private information to strangers. Many young people often piggyback on WiFi in public places and like test games. Loading and unloading software does not pay attention to safety and reliability. These behaviors may lead to the accidental leakage of personal information. At the same time, this also reflects that some of the functions of WeChat are defective, and there is a risk of leakage of personal privacy information.
Social Media Threats to User Privacy
Social media provide people with the new freedom of communication. Media are the primary driving force of social development, and the creation and use of each new medium announce that we have entered a new era (McLuhan, 1964). In the age of the Internet, everyone can enjoy the latest information and share their most timely ideas at any time. The boundaries between “communicators” and “receivers” are rapidly breaking down. On the one hand, the strong relationships established through social media platforms consolidate the network of acquaintances in the world. On the other hand, it accelerates the flow of information, generates more social consensus, and helps to eliminate barriers and obstacles between people. While people enjoy scientific progress, the risk of privacy also penetrates through the net into each individual who accesses the system.

Source:https://www.nationdigital.io/10_great_social_media_ideas_for_political_campaigns
The rise of social media has brought concerns about user privacy protection. In the era of social media, people begin to suffer from privacy anxiety. This anxiety comes from the fear that their activity information will be inexplicably collected, controlled, and disseminated online. Human concern about personal privacy has been formed since the information society. Persistence, searchability, and cross-indexability are the three distinctive features of privacy issues caused by information technology(Milne et al., 2004). The Internet itself pursues openness and sharing, which inevitably has the hidden danger of information leakage. Therefore, the privacy issues raised by social media are common to all Internet platforms.. At the same time, the characteristics of social media allow users to enjoy and sink into it. The openness and inclusiveness of social media determine the inevitable hidden dangers of information security because it further breaks the boundaries of space and time of privacy shielding, resulting in security problems for user privacy that are not limited to the traditional scope of personal privacy.
First, everyone who accesses the Internet gains the right to a voice, but privacy conflicts among users become acute and irreconcilable as the overall level of disclosure increases. The Internet easily enables connections between anyone. By owning a terminal with access to the Internet and registering an account with a social media tool such as WeChat, the Internet will take you to a whole new social world. Users can wander around the Internet to collect information about their targets. The privacy-violating party is caught in the dilemma of “stop socializing or put up with privacy violations.” Instead of fighting against powerful social platforms, users now have to guard against the unknown risks that any unfamiliar user in the Internet world may bring.
The second is the big data of social platforms. With the popularity of the Internet, many users are generating a large amount of data all the time. The amount of user-generated media uploaded to the web is growing rapidly, and no one can filter all media to see which ones affect our privacy(M. Smith et al., 2012). As a result, there are specialized data storage companies and data analysis companies independent of social platforms but maintain a considerable amount of privacy. These companies with data have created a “data privacy risk” with users that have never existed before. Currently, the ownership of data generated by users’ daily use is difficult to supervise and control, both from the legal and the actual operation levels.
Finally, it’s easy to connect anywhere at any time. No matter where you are at any time, social media’s instant location and sharing can find you and even show users around you. Social media enables the broadest reach of connectivity.
Countermeasures to address privacy information leakage
There are a series of privacy disclosure problems in the development of WeChat. Firstly, the WeChat software itself is flawed in its functionality. Secondly, users’ excessive privacy disclosure in use leads to the use of personal information by others. At the same time, there are also other problems, such as the influence of data and the lack of concepts and legal gaps. The maintenance of the network environment requires governmental system protection, the strengthening of the privacy concept of users themselves, the optimization of the platform, and other aspects.
Solving the privacy problem first requires the government to establish a long-term supervision mechanism, improve laws and regulations, and play the role of a supervisory subject. With the rapid development of the Internet, social networking software such as Weibo and WeChat have become prevalent. Although these applications encourage self-expression, they lack corresponding laws and regulations and protection mechanisms, and users cannot obtain a sense of private security in using them. The rules and regulations for information privacy in China are still relatively blank. We should speed up the improvement of information privacy laws and regulations and implement the responsibility mechanism.
Second, users need to raise their privacy awareness and pay attention to protecting private information. In the era of big data, we must control one’s privacy boundaries to prevent personal information from penetrating the public domain. People’s awareness of privacy boundary protection in the network world has blurred (Steeves & Regan, 2014). We need to change the wrong concept of privacy, raise our vigilance and maintain the right to privacy. Every social media user has the right to privacy, protects their privacy, and must not freely disclose and violate others’ privacy.
Third, strengthen industry self-regulation and optimize the functions of social platforms such as WeChat to protect users’ personal information from leakage. Operators should properly store users’ personal information, strengthen network security protection, and establish a special team to deal with privacy leakage issues. To optimize WeChat functions, WeChat can provide a humane way of managing user privacy. Enable some friends’ content blocking to help users understand the “boundaries” of their friends’ circle content. Regarding companies’ public interest obligations in digital media communications, an appropriate balance between company self-regulation and state regulation of digital platforms is required (Flew, 2021).
In Conclusion
The threat of digital privacy in social media is discussed with the example of information leakage caused by features in WeChat, and privacy leakage caused unintentionally by users’ use. User privacy in social media extends traditional privacy on social media platforms. It is a new development embedded in online privacy and social media tools’ attributes. Social media’s openness and inclusiveness determine the inevitable existence of information security risks because it further breaks the boundaries of privacy shielding space and time. Thus, the security problem of user privacy is not limited to traditional personal privacy.
Therefore, the maintenance of the network environment requires the institutional guarantee of the state and network platform builders, the users’ social media literacy, and marketers seeking a balance between precision marketing and privacy protection. These three parties only really have privacy protection as firmly rooted in every behavior to gain greater user trust in order to work together to create more significant breakthroughs in the future.
References
Flew, T. (2021). Regulating platforms (pp. 72–79). John Wiley & Sons.
Leubsdorf, J., & Westin, A. F. (1968). Privacy and Freedom. Harvard Law Review, 81(6), 1362. https://doi.org/10.2307/1339271
McLuhan, M. (1964). Understanding media: The extensions of man. New York : McGraw-Hill.
Milne, G. R., Rohm, A. J., & Bahl, S. (2004). Consumers’ protection of online privacy and identity. Journal of Consumer Affairs, 38(2), 217–232. https://doi.org/10.1111/j.1745-6606.2004.tb00865.x
Nissenbaum, H. (2009). Privacy in context: Technology, policy, and the integrity of social life. Stanford University Press.
Norberg, P. A., Horne, D. R., & Horne, D. A. (2007). The privacy paradox: Personal information disclosure intentions versus behaviors. Journal of Consumer Affairs, 41(1), 100–126. https://doi.org/10.1111/j.1745-6606.2006.00070.x
Smith, H. J., Milberg, S. J., & Burke, S. J. (1996). Information privacy: Measuring individuals’ concerns about organizational practices. MIS Quarterly, 20(2), 167. https://doi.org/10.2307/249477
Smith, M., Szongott, C., Henne, B., & von Voigt, G. (2012, June). Big data privacy issues in public social media. 2012 6th IEEE International Conference on Digital Ecosystems and Technologies (DEST). http://dx.doi.org/10.1109/dest.2012.6227909
Steeves, V., & Regan, P. (2014). Young people online and the social value of privacy. Journal of Information, Communication and Ethics in Society, 12(4), 298–313. https://doi.org/10.1108/jices-01-2014-0004