
Introduction
From the day the Internet came into our lives, we have entered the digital age, in which information technology is developing at a rapid pace. Through the online platform, we are both receivers and creators of information, and we are constantly engulfed in a flood of data. The internet is also like a transparent glasshouse, and we are the people who live in it. Even if you believe you are in a confined safe space, your every action can be monitored and digitized. The development of the digital age has not only brought unprecedented convenience to our lives, but it has also largely exposed the entirety of our personal information to the air, putting our privacy at high risk and under threat. Moreover, most people are unaware of how their private information was disclosed, when it was leaked and to what extent. Therefore, in this digital age, it is important for people to be aware of how their private information is threatened, while also raising awareness of personal privacy protection.
This blog will be divided into three parts. It will first explain the concepts of the digital age and the right to privacy; second, it will examine the threats to privacy in the digital age in specific cases; and finally, in the conclusion, it will discuss how to protect personal privacy in a digital age.
The Concepts of the digital age and the right to privacy
Before discussing and analyzing the topic of threats to privacy in the digital age, it is important to define two concepts – what is the digital age? What is the right to privacy? In simple terms, the digital age refers to a way in which information is present, where everything is based on electronic information and digital technology is used as a rule of operation, hence it can also be seen as the information age, while the Internet is a universal communication tool in the information age, with interactive and computerized characteristics (Kizilhan & Bal, 2016). As the Internet has become widespread around the world, information technology has brought a new form of social organization to the world – the network society (Kizilhan & Bal, 2016). The development of the digital age has brought unprecedented convenience and a new way of interacting with the world. In this digital age, when people are using their smartphones, computers, and other electronic devices actively, they are leaving a digital footprint on the internet, and all this information is turned into electronic data. This leads to the second keyword – the right to privacy in the digital age. There is no doubt that the right to privacy is a human right and that everyone has the right to be “left alone” (Warren, n.d.). The right to privacy in the digital age is also a derivative of human rights, and along with freedom of expression, everyone should be afforded due protection of their privacy, including, and not limited to the right to prohibit others from collecting, copying, using, and disclosing private information through illegal ways (Karppinen, 2017).
Specific cases of privacy threats: Facebook and Weibo
With the advancement of digital media, various social media platforms have inexorably infiltrated our lives, and it is no longer possible to avoid using social media platforms in both the workplace and personal life. Most people, especially those of a younger age, have a habit of sharing their daily lives on social media platforms such as Facebook, WeChat, and Weibo. As a result, there are concerns about online privacy. According to the data, although 67% of people are taking active steps to protect their personal privacy, for example, 61% of them have changed the settings on the social media they commonly use, but only 38% of people believe they can control their digital privacy information (Goggin, 2017).
Among the possible threats to privacy in the digital age, privacy disclosure has become one of the serious issues which are often discussed, with 78% of people curious about how their personal data is being handled by social media companies (Goggin, 2017). Through the frequent use of social platforms, digital platforms can easily collect a large amount of personal data about their users, for example by analyzing their interests and social circles through the people they follow or interact with, or even by inferring their personal family life, their regularly visited locations or even their political orientation through the posts they send and the type of news they focus on (Goggin, 2017). The platforms can analyze these big data to target content of interest to their users, for example by analyzing consumption habits to deliver relevant advertising. While this type of personalized promotion can be seen as positive when it is simply designed to increase interactivity by pleasing the user, the impact changes dramatically when such highly targeted content is mixed with politics.

https://pixabay.com/zh/vectors/facebook-logo-social-network-76658/
In 2018, a serious data leakage exploded on Facebook, which is one of the most influential social platforms in the world. This was caused by Cambridge Analytica violating Facebook’s data retention and collection policies by using the personal data of approximately 87 million Facebook users obtained during the 2016 presidential election to target them with politically directed campaigns without their consent, with the majority of those affected being American users (Confessore, 2018). The scandal has caused controversy since it was revealed that Facebook’s CEO Mark Zuckerberg has been requested to attend and testify before Congress (Confessore, 2018). How was this information collected from 87 million users? Zuckerberg claimed that Facebook began investigating “tens of thousands of applications” after the incident emerged (Confessore, 2018). Apparently, when users log in to those applications using their Facebook accounts, they leave a digital footprint, and this data trail contains a lot of private information about the user, which can be used to analyze their location (for example, the majority of those affected by this incident were American users) and political orientation. However, it is not known whether this data disclosure has materially interfered with the presidential election (BBC News, 2018). Nevertheless, the leakage of user data can also be seen as a misuse of personal data, which necessarily violates the user’s right to privacy. From the internet to big data, our personal data is playing an increasingly important role in electronic technology, and at the same time, more and more private data is being leaked in different places in different ways and used without the user’s permission, but the issue of data security protection has never been solved by a satisfying approach. It further illustrates that in the digital age, the protection of personal private data and the reduction of privacy threats is a constant challenge (Hinds et.al., 2020).
There are also threats to personal privacy on the Chinese social media platform Weibo. Among the many excellent features designed by Weibo, there are also two features that have caused user dissatisfaction.
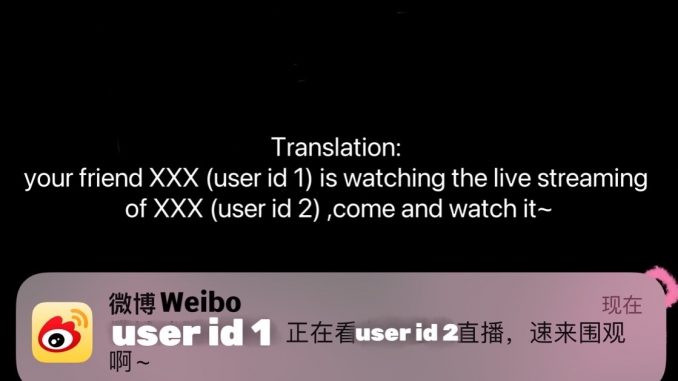
Screenshot of Weibo push notification
The first is Weibo’s push notification feature, which will send a message to a user’s followers when they are watching live streaming on Weibo – your friend XXX (user id 1) is watching XXX’s (user id 2) live streaming, come and watch it ~
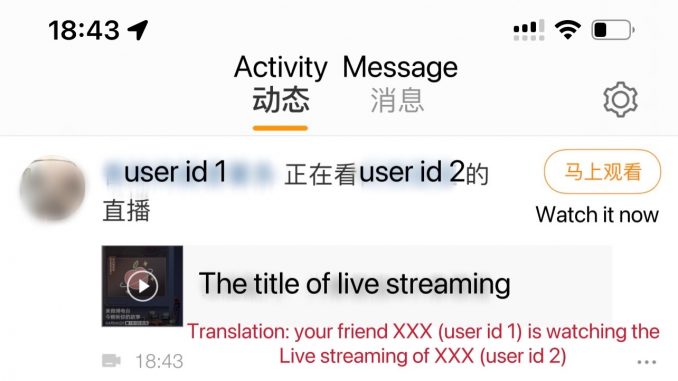
Screenshot of Weibo’s Activity page
When the followers of the user open Weibo, the Activity page on Weibo will display more detailed information, including the title of the live streaming, which means that the followers don’t need to join the live streaming room to know what the user is watching through this push notification. Although as a public platform it is essential to have push notifications that can increase the user’s activity and engagement. However, it is uncomfortable to distribute information about a user’s personal activity without their permission, and there is no way to turn it off or to request it from them before pushing.
This feature has similarities to Facebook’s Beacon service, which was released in 2007 and the service also sends information about users’ online purchases to their friends without their permission when they purchase products (Cohen, 2008). The service has also made many users feel that their privacy is being threatened. Just imagine if your friends told you that they had received a push message about your purchase when you were buying something that you didn’t want others to know about. Would you be outraged? This also leads to the importance of privacy boundaries, where users should have control over their privacy – should my personal information be made public? To what extent should it be made public? Who is allowed to see my personal information? The right to privacy is not only about the user’s right to be left alone but also about the user’s right to avoid threats (Goggin, 2017).
The second feature that has caused controversy is the display of the user’s IP location on Weibo’s personal information page, which is accurate to province/city for Chinese users and to the country for international users. Users who have used these social media platforms are aware that you can usually set your location on the personal information settings page, but the IP location is linked to the operator information and users cannot choose whether or not to disclose their IP location. As a result, the bulk of people is opposed to this feature, believing it violates their privacy.
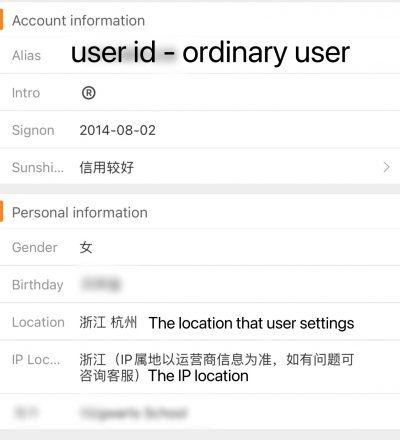
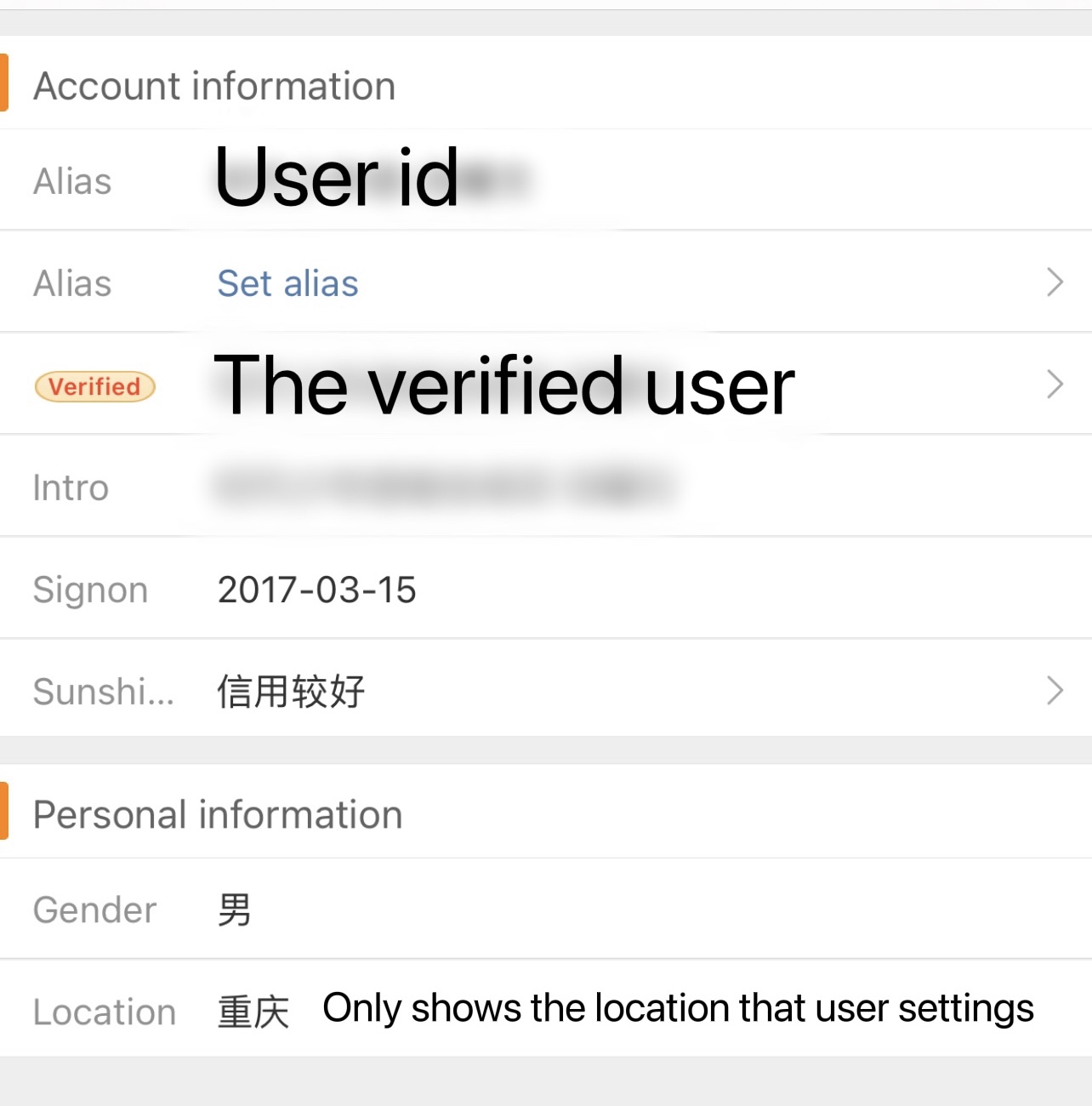
Screenshot of ordinary user’s personal information
Screenshot of the verified user’s personal information
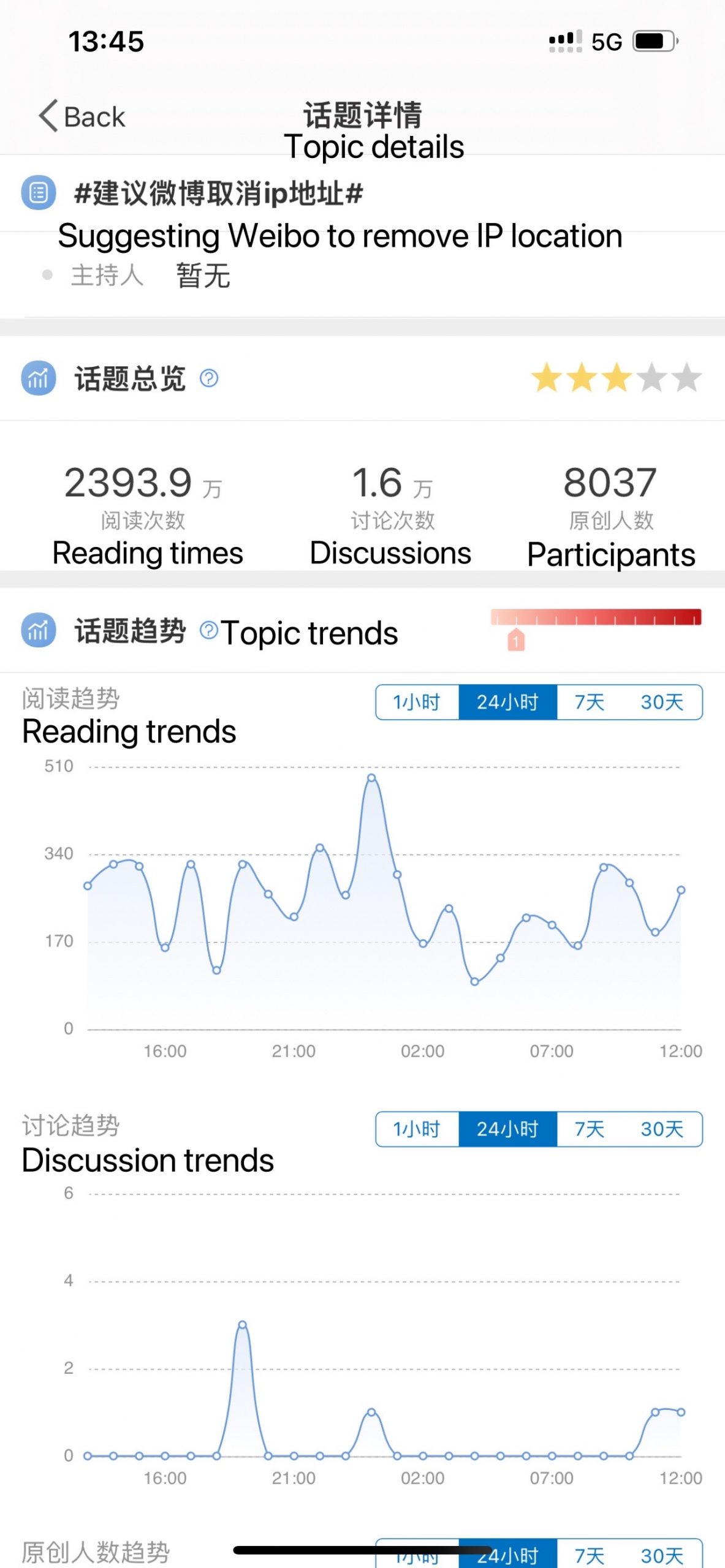
Screenshot of topic details
The topic “Suggesting Weibo remove IP location” has been read 23.939 million times and discussed 16,000 times on Weibo so far. Furthermore, some users have reported that while the IP locations of ordinary users are disclosed, the IP locations of verified Weibo users who have more than 500,000 followers are not, thus questioning whether Weibo is classifying people into different classes. When searching the keywords on Weibo about this case, we can see that many users are complaining about the perceived threat to their privacy and want to uninstall Weibo due to this. After all, not all users are willing to set their real location on the personal information page and it is clearly against their wishes to reveal their IP location directly.
All these cases illustrate the same point. In the digital age, it seems that our privacy is no longer under our control, and this can put our personal interests at risk. Even though the line between the right of access and the right to privacy has always been blurred and the conflict between them has been difficult to resolve (Davis & Cuillier, 2012). The right to privacy will always be seen as a vital right for us in this society and we should protect our personal privacy information.
Conclusion
In conclusion, it is undeniable that as the digital age continues to evolve, the call for privacy protection will become increasingly important (Davis & Cuillier, 2012). In Australia, most people are concerned about online privacy issues and worried about the government and companies posing a threat to their privacy (Goggin, 2017). How to protect ourselves from threats to our privacy in this seemingly transparent online age is a new challenge for everyone. It is essential that you provide your personal information carefully. For example, many applications have a privacy policy that needs to be confirmed by the user when registering, but most users skip this step and simply click to confirm, which is a very easy point to overlook in terms of privacy protection. Also, when visiting websites that require the personal information to be registered, be careful to check if they are legitimate websites to avoid privacy disclosure. A strong password rather than a simple combination that can be easily hacked is also a good idea and change your password regularly. It is also increasingly important for the government to strengthen the regulation of social media platforms, and to manage users’ private data by giving them the right to know when they need to use their private information and give users’ the right to edit this kind of private information so that they can decide for themselves whether to disclose the private information and thus reduce threats such as privacy leaks.
Bibliography
BBC News. (2018, April 4). Facebook scandal ‘hit 87 million users’. BBC News. Retrieved from https://www.bbc.com/news/technology-43649018
Cohen, A. (2008, February 18). One Friend Facebook Hasn’t Made Yet: Privacy Rights. The New York Times. Retrieved from https://www.nytimes.com/2008/02/18/opinion/18mon4.html
Confessore, N. (2018, April 4). Cambridge Analytica and Facebook: The Scandal and the Fallout So Far. The New York Times. Retrieved from https://www.nytimes.com/2018/04/04/us/politics/cambridge-analytica-scandal-fallout.html
Davis, C. N., & Cuillier, D. (2012). Transparency 2.0: Digital Data and Privacy in a Wired World (1st, New ed.; C. N. Davis & D. Cuillier, Eds.). New York: Peter Lang Inc., International Academic Publishers. https://doi.org/10.3726/978-1-4539-1333-8
Goggin. (2017). Digital Rights in Australia. The University of Sydney. https://ses.library.usyd.edu.au/handle/2123/17587
Hinds, J., Williams, E. J., & Joinson, A. N. (2020). “It wouldn’t happen to me”: Privacy concerns and perspectives following the Cambridge Analytica scandal. International Journal of Human-Computer Studies, 143, 102498–. https://doi.org/10.1016/j.ijhcs.2020.102498
Karppinen. (2017). Human rights and the digital. In H. Tumber & S. Waisbord (Eds.), The Routledge Companion to Media and Human Rights (pp. 95–103). https://doi.org/10.4324/9781315619835
Kizilhan, T., & Bal Kizilhan, S. (2016). The Rise of the Network Society – The Information Age: Economy, Society, and Culture. Contemporary Educational Technology, 7(3). https://doi.org/10.30935/cedtech/6177
Warren, S. D. (Samuel D., & Brandeis, L. D. (n.d.). The Right to Privacy. Project Gutenberg.