Introduction:
With the continuous development of technology, today’s society has entered the digital age. So, what exactly is the digital age? According to Barrett’s introduction, the digital age is an economic-based historical period based on information technology and the miniaturization of computers (2015). In this era, human life is inseparable from information technology everywhere. Well-known media platforms like Instagram and Facebook have become the most common social tools used by modern young people. TikTok, as the most popular short video platform at the moment, according to data, as of March 2022, the number of active users has reached one billion (Brandon, 2022). And these users are all registered users on TikTok. That means they entered some personal information on TikTok. At the same time, these users are mainly composed of children and teenagers who do not pay enough attention to privacy issues. Thus, the threat of privacy issues arises. This blog will discuss and analyze the threat of privacy issues caused by information technology in the social media, using the privacy issues caused by TikTok as a case.
Privacy issues with TikTok:
Figure 1
According to information published by mobile marketing company URL Genius, new research shows that TikTok allows third-party trackers to collect users’ data (Tom, 2022). At the same time, users have no way of knowing who is tracking and what information they are tracking. Not only that but Wired also even speculates that TikTok will share user data with other companies. With this threat in mind, then-President Trump considered banning TikTok in the United States in 2020. But current President Joe Biden withdrew the proposal and issued a decree reviewing the privacy and security of all foreign-owned software.
Not only that, but according to Security.org reporter Aliza Vigderman, TikTok can collect as many as 50 different kinds of personal information from users 13 and older (Dave, 2021). Not only that, but the information also collected from users will be shared with third-party companies such as advertisers, analysts, suppliers, etc. However, it is unknown what third-party companies will do with user information. Many American politicians believe that TikTok’s parent company is spying on American citizens by mining users’ data. Therefore, the privacy issues raised by TikTok also involve national security.
It can be seen from the above reports that social software like TikTok that needs to collect user information involves privacy and security issues. There are many more such reports. Users and even countries are threatened by the leakage of information. So how do users and society react to this?
Users and society react:
First of all, according to Geoffrey, the US government began to consider banning the use of TikTok in 2020 (2020). In July of the same year, the Democratic National Committee warned staff not to use TikTok. In addition, as a similar social media platform, Amazon also prohibits employees from downloading TikTok on work phones. Not only the United States, but other countries such as India are gradually banning the use of software such as TikTok.
In addition to some government and official restrictions, many users have stopped using TikTok due to privacy concerns. For example, gaming star Ninja tweeted that he had deleted TikTok. In doing so, he is also calling on his fans to take privacy seriously. Since many TikTok users are minors, parents also attach great importance to the privacy of their children. Some parents have banned their children from using TikTok.
Not only TikTok, but similar social media software has seen boycotts from governments, officials, and users. And most of the reason for this phenomenon is because of concerns about privacy issues. So why do these software have privacy problems?
Reasons for privacy concerns:
- First of all, the basic reason for the emergence of privacy problems is because of the massive use of information technology. Before these softwares are used, people don’t have to worry about personal information being leaked, because normally no one can get other people’s personal information. This is also the root cause of privacy concerns. Taking TikTok as an example, the number of users who use it has grown at a significant growth rate. The figure below is a data record from the TikTok Report, which Mansoor said will continue to grow (2022). This shows how much modern people rely on social media. Because so many people use and cannot give up online technology, social media has the opportunity to use user information. Massive use of information technology, this is the basic reason for the emergence of privacy problems.
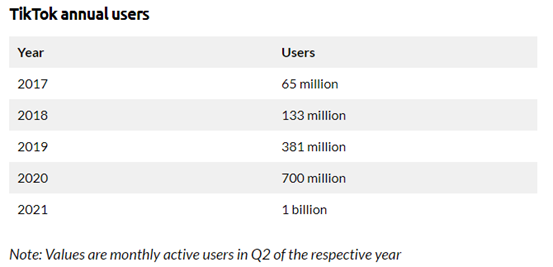
Figure 2
- Secondly, the emergence of privacy problems is because these social software needs to collect a lot of information from users. The first step for users to use social software is to register an account. In this process, basic information such as name, birthday, etc. will be entered into the system. In many cases, this information will be published to all users with the creation of the account. For example, after a new user registers a TikTok account, other users can browse the personal information on the user’s personal homepage if they do not set up any further. Not only that, in later use, these software will use the user’s account as data, and use algorithms to improve the service. Just like TikTok, according to Jessica, TikTok will use algorithms to recommend services or content for users based on their usage habits and data (2022). Although this method improves the user’s experience, it also violates the user’s privacy invisibly, because the user does not agree with them to do so. The use of social media is a process of interaction with users, and when the interaction occurs, information is generated. Therefore social media software such as TikTok can obtain a large amount of user information, and thus threaten the user’s privacy.
Why should privacy concerns be taken seriously?
When privacy concerns are raised, rights have to be taken seriously. According to Karppinen, individuals have various rights in society (2017). While these rights protect individuals, they also limit individuals. First, from the user’s perspective, users have the right to the ability to protect themselves from unnecessary censorship by others. This means that without the user’s consent, other people should not access any of the user’s information without the user’s violation of regulations or laws. As mentioned above, some social media software access users’ information without authorization to provide better service and thus increase customer satisfaction. The purpose of this action is in the interests of the company. The user did not perform any illegal operations during this process, so this behavior is an invasion of privacy. Just like TikTok, according to Christina, TikTok will recommend new content for users based on what users follow or block (2022). This content is not supposed to be accessed without the user’s permission. Therefore, this behavior violates the user’s privacy. Not only that, but users also have the right to control how their personal information is used. As mentioned above, many companies are sharing their user information with each other for some benefit. This behavior is without the user’s consent, and they have the right to refuse their use of personal information. Therefore, the user’s privacy is violated.
Although most of the public information shows that software operators share user information with third-party companies, the main purpose is to improve services and make user experience better. However, no one can know whether the shared information will be re-shared with third-party companies. Sharing again may cause harm to users. During these processes, the user did nothing wrong. Therefore, privacy issues are very important for everyone. That being the case, how should privacy threats be managed?
Figure 3
How to manage the privacy threats:
- On the government side:
Everyone’s right should be the government’s attention, and as such, governments need to make changes in how they manage privacy threats. First of all, the US ban on TikTok mentioned above is an inappropriate approach. While TikTok can raise some privacy threats, governments should not ban one or more companies from operating their social media without hard evidence. This not only violates the rights of the company to which TikTok belongs, but also deprives individuals of the right to use TikTok. Therefore, this approach is not a good solution to privacy threats. According to Damien, the government should set up policies for cyber privacy security issues (2019). Since the government can enforce mandatory management of companies, the copy issued by the government is the most authoritative. Any foreign company operating in a country needs to follow local laws and regulations. Therefore, governments of all countries should pay attention to the issue of online privacy and establish laws and regulations to protect the privacy of users.
- On the corporation side:
Furthermore, privacy concerns are a top priority that every business should consider. Although data and information technology companies in today’s society provide people with many novel and convenient services, their main purpose is to make profits. Most software will expose privacy rules to users. However, these privacy regulations are often imperfect. Take TikTok as an example. According to Tom, the official information released by TikTok indicates that they will share user information with Google, Apple, Snap and AppsFlyer (2022). While they say the shared information is used to measure the performance of campaigns on social media platforms, no one has looked into what the four third-party companies do with the shared information. At the same time, TikTok does not have any rules to bind these third-party companies to keep the shared information confidential. Even, there is no way to guarantee the network security of these third-party companies. The user’s information is likely to be leaked out, thereby causing harm to the user. Therefore, as the company that users use the product, they have the obligation and responsibility to protect the privacy rights of users. These companies should first obtain the user’s permission before using any user information. As mentioned above, many companies have unauthorized access to user information for use in algorithms. This behavior should be banned. Second, these companies should reach legally effective agreements with third-party companies that the shared information cannot be leaked. All in all, whether it is to improve service quality or for other purposes, information technology companies should take the privacy rights of product users as the most important protection goal.
- On the user’s side:
Finally, users should also raise their awareness of protecting their privacy. According to Laurel’s report, conducting a privacy breach survey found that 74% of people were unaware that their information was compromised (2021). In fact, everyone wants their privacy to be protected. But many times, they are unaware that some of their actions will lead to privacy issues. For example, users simply fill in some personal information on TikTok to introduce themselves to other users. However, such personal information may be used improperly to pose a threat to users. It can be seen that users should raise their awareness of protecting their privacy.
Conclusion:
In conclusion, in today’s society, with the rapid development of information technology, network technology has been integrated into people’s lives. As an information technology with a large number of users, social media not only facilitates people’s lives, but also brings privacy threats. Just like TikTok, they violate user privacy in some algorithm or rating process. Privacy issues involve individual rights, so everyone should take it seriously. Although some governments and users have taken some action against privacy threats today, it is obviously not enough. Governments should issue laws and regulations specifically addressing online-related privacy issues to protect users. Information technology companies should also strengthen the protection of user privacy. But the most important thing is that users should raise their awareness of protecting privacy.
Reference List:
- Barrett, Michael, Davidson, Elizabeth, Prabhu, Jaideep, & Vargo, Stephen L. (2015). Service Innovation in the Digital Age. MIS Quarterly, 39(1), 135-154. Viewed on 04/04/2022. Retrieved from https://web.s.ebscohost.com/ehost/pdfviewer/pdfviewer?vid=0&sid=4a5b2740-bfe2-4c43-a7ee-c9c0af38be02%40redis
- Brandon, D. (2022). TikTok Statistics – Updated March 2022. Viewed on 04/04/2022. Retrieved from https://wallaroomedia.com/blog/social-media/TikTok-statistics/#:~:text=TikTok%20is%20available%20in%20over,in%20the%20United%20States%20alone.
- Tom, H. (2022). TikTok shares your data more than other social media app – and it’s unclear where it goes, study says. Viewed on 04/04/2022. Retrieved from https://www.cnbc.com/2022/02/08/TikTok-shares-your-data-more-than-any-other-social-media-app-study.html#:~:text=As%20CNBC%20noted%20last%20year,%E2%80%9Csafeguard%20sensitive%20user%20data.%E2%80%9D
- Dave, J. (2021). Is TikTok safe? Here’s what you need to know. Insider. Viewed on 05/07/2022. Retrieved from https://www.businessinsider.com/is-TikTok-safe
- Geoffrey A, F. (2020). Is it time to delete TikTok? A guide to the rumors and the real privacy risks. The Washington Post. Viewed on 05/04/2022. Retrieved from https://www.washingtonpost.com/technology/2020/07/13/tiktok-privacy/
- Mansoor, I. (2022). TikTok Revenue and Usage Statistics(2022). Business of Apps. Viewed on 05/04/2022. Retrieved from https://www.businessofapps.com/data/tik-tok-statistics/
- Jessica, W. (2022). How Does The TikTok Algorithm Work? Here’s Everything You Need To Know. LaterBlog. Viewed on 05/04/2022. Retrieved from https://later.com/blog/tiktok-algorithm/
- Karppinen, K. (2017), Human rights and the digital. In Routledge Companion to Media and Human Rights. In H. Tumber & S. Waisbord (eds) Abingdon, Oxon: Routledge pp 95-103. Viewed on 06/04/2022. Retrieved from https://www-taylorfrancis-com.ezproxy.library.sydney.edu.au/books/edit/10.4324/9781315619835/routledge-companion-media-human-rights-howard-tumber-silvio-waisbord
- Christina, N. (2022). How the TikTok Algorithm Works in 2022 (and How to Work With It). Hootsuite. Viewed on 06/04/2022. Retrieved from https://blog.hootsuite.com/tiktok-algorithm/#:~:text=What%20is%20the%20TikTok%20algorithm,your%20current%20state%20of%20mind.
- Damien, M. (2019). Seven ways the government can make Australians safer – without compromising online privacy. Viewed on 07/04/2022. Retrieved from https://theconversation.com/seven-ways-the-government-can-make-australians-safer-without-compromising-online-privacy-111091
- Laurel, T, M. (2021). People don’t realize they’re data breach victims. Viewed on 08/04/2022. Retrieved from https://www.futurity.org/data-breaches-personal-information-2587202-2/
- (Cover Figure). Community. (2021). How Free & Open Source Software Can Save Online Privacy. Viewed on 08/04/2022. Retrieved from https://news.itsfoss.com/save-privacy-with-foss/
- (Figure 1). Geoffrey, A, F. (2020). Is it time to delete TikTok? A guide to the rumors and the real privacy risks. Viewed on 08/04/2022. Retrieved from https://www.washingtonpost.com/technology/2020/07/13/tiktok-privacy/
- (Figure 3). Chia, S, C. (2018). Reflecting on online privacy and protection for teachers and students. Viewed on 08/04/2022. Retrieved from https://www.modernenglishteacher.com/reflecting-on-online-privacy-and-protection-for-teachers-and-students

