

INTRODUCTION
As the internet reaches more and more aspects of our lives, we are led to believe that we are safe within the comforts of our house, away from prying eyes, and free to click, watch, type, and “add to cart” whatever we want. In the thrill of being entertained with lots of appealing content, we forget to pay attention to details about how our preferences and private information are protected (or abused) by the online platforms that we use and enjoy.
Privacy is something we associate with the feeling of being safe and secure. When we say privacy, we are painting a mental image of being comfy in our space like our rooms or cars, without anybody watching, without anybody judging, and without anybody violating our safe space.
However, it could be argued that our privacy is ironically being threatened by the online world that we hide in to get away from the watchful public. In the online sphere, every piece of personal information we provide, every word we search, and everything we click on or react to, or share with our friends are recorded as statistical data, collected by the platform owners, and analyzed in order to target specific people with specific advertising (Flew, 2018). This collection of personal information collected by online platforms is called “big data analytics.”
Essentially, big data analytics means the high-speed analysis of large quantities of data taken from users of an online platform to make patterns about the consumers’ habits more observable (Mikalef et al., 2020). In order to get this data collected, websites and online platforms use cookies, super cookies, and other “smart” tools that could be privacy-invasive when left unchecked.
This blog will lay down academic papers and case studies that would illustrate the thesis that online platforms do not prioritize our privacy over their potential economic or strategic gains which puts pressure on us to step up our vigilance in addressing the things that threaten our privacy in this digital age.

Cookies and Supercookies record users’ activities and preferences to give website owners collected data that could be sold to third-party websites and advertisers. Szyszka (2015)
Cookies and Supercookies are not as great as they sound
Cookies sound sweet and innocent to us computer muggles, but to paint a better picture, forget the tasty “cookie” that we get as treats from grandma and imagine a virtual “Kookie” —a creepy person who follows you around when you enter a store (or a website) and writes down everything you see, touch, and like, and reports them back to the store’s owner so that the owner could then pick out things that you might like and have them displayed much closer to you than ever before. It sounds harmless, even convenient when you think about it. Until the owner decides to sell the information that the Kookies collected to other store owners, advertisers and door-to-door solicitors so that they can shove their own products to your face, wherever you are, whomever you are with, or whatever you are doing (Wagner, 2020).
Supercookies or Permacookies are an even creepier version. While cookies start tracking your movement when you enter the store (website) and stops spying on you when you leave, supercookies track everything you do in the store, but will follow you to your car, goes in with you, records all the routes you take, all other shops you visit, the food you order and at which times, the types of music you listen to, the friends and family members you frequently contact, your home and work address, and all your magazine subscriptions, among other internet stuff you might prefer to keep to yourself (Wagner, 2020).
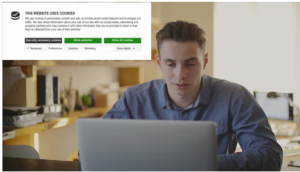
Visitors of most websites see pop-up banners telling them to enable cookies. Shutterstock/Cookiebot CMP
Privacy is the price of convenience
By my description, you may be thinking, if cookies, supercookies and other tools websites use invade my privacy, shouldn’t I be asked to give my consent before these things can start tracking me? The answer is YES. And they do ask for your consent. Usually, when we log on to most websites, we are greeted by a banner like in the picture above, basically saying that we need to voluntarily allow the website to give us “cookies” in order for us to fully experience the best service of the website with content or services that we like without having to spend a lot of time and clicks before getting to the good parts. Because most of us have been desensitized to boxes with the “allow” or “don’t allow” (pop-up dialogues) that pop-up before we are able to use the websites and all its features properly, we tend to keep clicking “agree”, or “accept” without reading the text.
What we do not know (or don’t care about) is in order to make our browsing experience more convenient, we sacrifice a little bit of our privacy to help the website “understand” the things we like and “predict” content that we would find interesting. We nonchalantly allow all cookies and enjoy content that have been tailored to our preferences. But what we do not see in the pop-up dialogue is the detailed (and sometimes purposefully boring) declaration of how cookies record our data and compile them to be sold to third party advertisers or platforms that could use this data to conduct targeted advertising or even send promotional materials or scams to our personal emails and contact numbers. Legally speaking, we cannot complain about cookies and supercookies tracking our activities and consequently selling that data to other companies because we virtually “allowed” them to do so (Seuchter, 2020). Nonetheless, there is a looming threat of online companies and platforms abusing our negligence of our online data’s privacy and security.

Yahoo! Previously known as the best E-mail service provider got in trouble for looking through over 500 million users’ emails and turning them over to the NSA without the users’ permission. The Bottom Line (2015).
Yahoo, Verizon, and Vizio have already started (and got busted) violating our privacy
Aside from cookies, which, we “allow” to track our virtual life decisions, some companies have already been caught violating their users’ privacy, in one form or another, without the users’ consent.
On October, 2016, Yahoo was exposed by Reuters for scanning emails of users without their permission and having that data sent to the National Security Agency (NSA). While the invasion of privacy was done under the premise of “National Security”, it is undeniable that the privacy of millions of users was breached. Imagine having your postman deliberately opening your mail and telling the NSA about what he or she found, all without you knowing any better (Kolevski et al., 2021).
Verizon practically created the supercookie in order to have more information on their customers’ browsing history without their knowledge. After being fined by the Federal Communications Commission $1.35 million fine, Verizon was forced to alter their policy to give customers the liberty to choose to be or not to be tracked by the supercookie. Even then, the fine seemed negligible but the Verizon supercookie already inspired a lot of like-minded companies to create their own version and use it for their own gain (Andreotta et al., 2021).
Lee et al. (2019) highlights Vizio, maker of smart televisions, in a case study in which Vizio has also been caught violating the privacy of their clients. Allegedly violating the Video Privacy Protection Act, Vizio was found recording its users’ details and disclosed that information to third party advertising companies that send out targeted ads to the same clients. It is scary to think that TV companies are also watching you when you watch your favorite shows and take note.
These particular cases and the studies they warranted all lead to a generalization that stricter regulations must be implemented, but at the same time, we must acknowledge the importance of protecting our private information and do our part to limit the greedy ones from blatantly invading our privacy.

Figuring out what to do to protect yourself from privacy violations can be very frustrating. Cobalt Blog (2016).
Where do we go from here? What can we do?
As mentioned in Terry Flew’s Platforms on Trial (2018, pp 28-29), Arie Freiberg (2010) suggested that at times such as this, the concepts of soft-law and co-regulation is the safest way to go. Soft-law, according to Freiberg (2010), is the collection of norms, practices and other social behaviors that encourage the protection of privacy developed by the internet community in a somewhat cultural manner. It would be like we, the people of the internet, developed our set of behaviors to encourage how to treat others online, with the addition of quasi-judicial entities empowered by the government to enforce the agreed upon form of regulation. Co-regulation proposes that without waiting for the government’s mandate, the owners of social media platforms and other websites ought to conduct themselves with some level of transparency acceptable to the people especially as to how they treat data collected from the people (Freiberg, 2010).
It is undeniable that the governments have the ability to crack down and sanction companies that are out to deliberately violate our privacy, as seen in the examples I mentioned above. However, it is also clear that they will not be able to bite the gigantic corporate hands that feed them millions of dollars in taxes and electoral advantage (Flew, 2018, p. 24). This means that while we wait for the government to find the middle ground where some degree of privacy is willingly surrendered by the people for the consumption of the big data industry, and company owners commit to being accountable and transparent with their use of our data, we must put up our own defenses to safeguard the aspects of our privacy we wish to preserve that the government does not pay much attention to.
Even without elite level computer skills, here are 3 things we can do to safeguard our privacy.
1. Learn how to delete cookies and supercookies from your computer from Youtube, etc.
Using Youtube to gain essential skills is now a common practice for those with at least a decent internet connection. It is a convenient way of learning the step-by-step process of removing cookies and even supercookies. Learning to do things from Youtube is now a common practice. If you don’t do this already, it is never too late to start.
2. Use a VPN provider.
Supercookies and other invasive programs can dig up our private information, this includes our home or addresses. Using a VPN or Virtual Proxy Network will mask our actual location and replace it with a random IP address to fool the supercookies. Aside from this, legitimate VPN service providers include a number of security measures that help protect ourselves from invasive and malicious entities (Iqbal & Riadi, 2019).
3. Read Privacy Policies and Terms of Use presented by websites and companies.
To regain some of our security and privacy, we must take it upon ourselves to read the specifications of privacy policies, terms of use and other declarations made by the websites we frequently visit. Even though it is boring or tedious, we need to arm ourselves with the vigilance to recognize and even call out those that dare to take advantage of our desires to be entertained, to shop, and to communicate with our loved ones, especially if it is for personal financial gain.
CONCLUSION
At the end of the day, our personal preferences and media consumption information may not be qualified as a pressing national concern that would spur the government to prioritize strengthening the existing regulations for privacy protection, it is, however, very important to us, as human beings, to preserve our right to not be taken advantage of, and exercise our liberties in private. And so, it must fall unto us to be more vigilant in order to protect ourselves and our loved ones from threats to our privacy in this digital age.
REFERENCES
Andreotta, A. J., Kirkham, N., & Rizzi, M. (2021). AI, big data, and the future of consent. Ai & Society, 1-14.
Flew, Terry (2019) ‘Platforms on Trial’, Intermedia 46(2), pp. 18-23.
Flew, T. 2018. Regulation. InterMEDIA. 46 (2). pp24-29.
Freiberg A (2010). The Tools of Regulation. Federation Press.
Iqbal, M., & Riadi, I. (2019). Analysis of security virtual private network (VPN) using openVPN. International Journal of Cyber-Security and Digital Forensics, 8(1), 58-65.
Kolevski, D., Michael, K., Abbas, R., & Freeman, M. (2021). Cloud Data Breach Disclosures: the Consumer and their Personally Identifiable Information (PII)?. In 2021 IEEE Conference on Norbert Wiener in the 21st Century (21CW) (pp. 1-9). IEEE.
Lee, J. J., Frumkin, K. B., Tran, S., & Sanchez-Mandery, N. (2019). Consumer Protection in the New Economy: Privacy Cases in E-Commerce Transactions or Social Media Activities. CONSUMER FIN. LQ REP., 73, 6.
Man dangling behind employee. Adapted from “Time-tracking Allows Monitoring Employees Completely Legal” by J. Szyszka, 2015.Timecamp. Retrieved on April 4, 2022, from https://www.timecamp.com/blog/2015/05/time-tracking-allows-monitor-employees- completely-legal/me tracking allows you to monitor employees – is it completely legal?
Man looking at computer. Retrieved on April 6, 2022, from https://th.bing.com/th/id/
R.3f0b3f277055be4c24bcd01096da4069?rik=iBzhK3k2cyA3qQ&riu=ht tp%3a%2f%2fak1.picdn.net%2fshutterstock%2fvideos%2f11114321%2fthumb%2f1.jpg &ehk=r% 2bHSNgddKtF2%2fRpxMxXpH%2fdCM69p9n1rKSecoWzWSfI%3d&risl=&pid=ImgR aw&r=0
Mikalef, P., Boura, M., Lekakos, G., & Krogstie, J. (2020). The role of information governance in big data analytics driven innovation. Information & Management, 57(7), 103361.
Privacy issues digital image. Adapted from “Privacy Issues and Solutions for Consumer Wearables,” by A. Perez, 2018. IEEE Computer Society. Retrieved on April 6, 2022, from https://publications.computer.org/it-professional/2018/09/06/privacy-issues- solutions-consumer-wearables/
Seuchter, G., Prossnegg, S., Beimrohr, V., & Branley-Bell, D. (2020). The Crux of Cookies Consent: A Legal and Technical Analysis of Shortcomings of Cookie Policies in the Age of the GDPR. Jusletter IT.
Wagner, P. (2020). Cookies: Privacy Risks, Attacks, and Recommendations. Attacks, and Recommendations (December 8, 2020).
Woman frustrated in front of computer. Adapted from “3 Common Problems AMS Users Run Into”. Cobalt Blog. 2016. Retrieved on April 3, 2022, from https://www.cobalt.net/3- common-problems-ams-users-run-into/
Yahoo CEO addresses audience amid data breach. Retrieved on April 4, 2022 from yahoo.https://miro.medium.com/max/1400/1*SMJy84UzbgnGIeJYdc2MoA.jpeg