Introduction
In the past, personal data was mainly stored on physical media. The rise of the Internet has had a profound impact on the storage and use of personal data. With the complexities of modern emerging technologies, realization of many life scenarios relies on the collection of personal data. For example, in order to closely monitor users’ bodily functions, wearing a smartwatch will be a popular choice. This kind of watch will record and warn physical data like heart rate and sleep quality, so users can make plans easily based on personal data.
However, the initiative to protect personal data is no longer in users, but in data controllers. The public’s serious concern about the abuse of personal privacy is a problem that governments and society cannot ignore.
This article will take Twitter as an example to explore the main manifestations of personal data misuse by individuals, platforms or institutions, as well as the existence of terms of service and the lack of data regulation, and finally discuss some possible solutions.
How to define data misuse?
We should distinguish data theft and data misuse. Data theft is that bad actors obtain personal data without permission. Data misuse refers that when information that was legally collected is used in ways beyond the original purpose, which is the most obvious difference between data misuse and theft. Odusote (2021) mentions that if such data is used outside the scope of agreements, policies or laws, the misuse of data will occur.
According to the research, there is also the obvious phenomenon that data misuse tends to be concentrated on large Internet media platforms because of the resulting unequal data advantages derived from the benefits of new media access, which is called ‘the digital divide’ mentioned by Flew (2014). He goes into more details that inequalities in the digital environment not only brings social gap but also reflects inequal digital sources. Therefore, Internet giants have a huge user base and is constantly attracting new user groups, which has a natural and huge advantage in collecting user data, meaning that they should take more responsibilities on avoiding the misuse of personal data.
Ways of the misuse of personal information
As an Internet platform, Twitter’s misuse of personal data is complex and mixed.
Most people will have this experience: When registering as a member or shopping online, it is possible to receive harassing phone calls, endless spam and SMS promotions in a short time. For data controllers, the sale on personal data at large scale has also become another point of interest delivery, thus making data misuse possible. Walrave, Vanwesenbeeck and Heirman (2012) point out that personal data posted by users on Social Networking Sites can be used by information predators on the Internet for illegal and incorrect purposes.
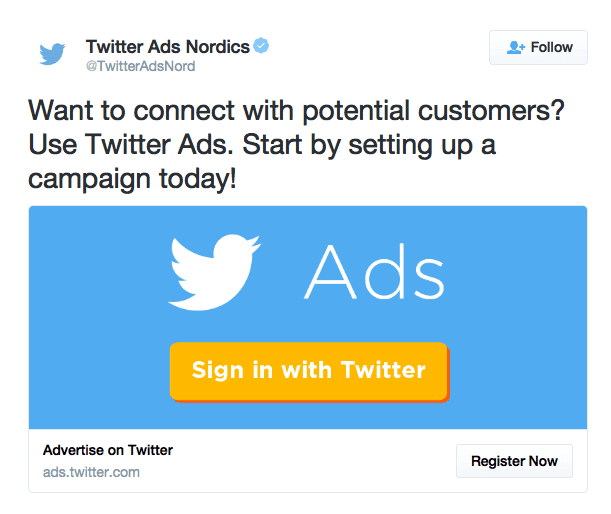
Image 1 Ads of Twitter link: https://adespresso.com/wpcontent/uploads/2016/02/Twitter_Ads_Nordics.png
Twitter initially insists that personal data is collected solely for the benefit of users in order to provide and improve the service experience that the platform gives them (Idjeri, 2018). However, in September 2019, Twitter issued a statement acknowledging that its partnership with advertisers, which allows advertisers to access their user personal data in order to improve the accuracy of the intended audience and improve the targeting of advertising marketing. In fact, Twitter obtains relevant personal information, including phone numbers, email addresses and even all property information, and then Twitter submits commercial quotations for advertisers. The result is that user information has already been quickly circulating and being valued, bought and sold for commercial purposes. Marketers can also use Twitter’s database to add consumers’ personal information to their detailed profile, linking to additional information about their identity and web browsing activity (Brain, 2019). In reality, some enterprises, institutions and even individuals, for commercial interests, randomly collect, illegally obtain, overuse, illegally trade personal data, and harass public lives.
Another scenario that typifies data misuse is customized service on media platforms and with it comes the challenge of improper data handling behaviours. With the development of technologies, intelligence and personalization are increasingly wrapped around and improve every aspect of our lives. Every click or browse of the user is not meaningless, it also is the personal data that the platforms can collect in the background, and then they can quickly describe the virtual personal images, buying habits, or even daily life routines through algorithms, for example, search for a product online and then receive repeated ads for the same products. Internet companies are used to manipulating platforms to carry out commercial marketing and information push based on personal characteristics through automatic decision-making without any third-side governance, which is a kind of secondary use of personal data. Many negative problems arise in the process of over-reliance on personalized recommendations. When provided information and content are in their own small circle called ‘information cocoon’ for a long time, their life will take on a formalization and routinization. In such a closed environment, different or competitive information, concepts or beliefs are examined, denied or cannot be fully expressed, and their personal thinking ways are bound to regard these prejudices as truth, and then excluding the invasion of other quite reasonable views, which easily evolves extreme thoughts and behaviours.
Why users can’t protect their personal data?
In many cases, data owners actively or passively ignore the importance of service agreement, making laws or rules difficult to defend their fundamental rights. Every time users need to use a software or download a free application, they have to agree to the terms of services provided by the platform in advance, and these terms usually include notification of personal information collection service. Suzor & Nicolas (2019) figure out that terms of service are contractual documents that establish simple consumer transactions: in exchange for access to the platform, the user agrees to be bound by the terms and conditions listed. Robinson & Zhu (2020) both refer that although these provisions are important and the content usually involves some sensitive personal information, studies have shown that most users rarely read the terms of service and carefully think about the meanings. Maybe they complain its length, feel confused about this legal document and don’t want to review it. Maybe the vast majority of people did not question it, and no one seems to have suffered any terrible consequences from signing it. In fact, as long as the user checks the consent button, and then platforms can collect individual data mandatorily without any legal responsibilities.
Obviously, the service agreement is in opposition to the user’s interests. Pasquale (2015) considers powerful businesses or institutions hide their behaviours behind confidentiality agreements, proprietary methods and rules. Our own life is becoming gradually transparent, and everything we do on the Internet is being recorded. The process of using personal data by platform operators and agencies is in secret, like a black box under the terms of service. They provide inadequate information about the purposes for which the data is processed, and the public, in contrast, couldn’t know anything about data how they collect, how they use, or whether they have spread out.
Another factor is that data controllers are not users, and platforms don’t acknowledge that they have an obligation to maintain data security, just as Twitter claims to be just intermediaries that provide technology. However, the public has been exposed to a number of events and scandals over the past few years which have raised concerns about dataveillance (Lupton & Michael, 2017). The lack of data governance makes it easier for individuals or organizations to use the platform’s data repeatedly.

Image 3 Mobile Phone Privacy Leak link: https://mandarinbean.com/wp-content/uploads/2020/02/5101.jpg
For example, Twitter’s service agreements tacitly allow they can transfer their personal data to third-party countries, but do not ensure the ability of those countries to protect data security. In June 2020, Twitter announced that their billing information involved some personal data of some accounts was leaked in New Delhi (Mint, 2020). If a user checks billing information on a website that logs in to Twitter, there is a good chance that the information is already stored in the browser’s cache. When others use the computer again, cached information in the browser can be discovered.
In addition, People who have access to personal data can illegally obtain and use personal data for their own benefit, which usually involves hackers or company employees. In July 2020, Twitter has revealed that there were up to 130 accounts stolen by cyber attackers through a tool called “Your Twitter Data”, and some of them were official personal accounts. Surprisingly, these users were unaware of the stolen accounts because they did not receive any verification and alerts. Hannah (2020) mentions the hackers reset their passwords, logged into the user’s account and sent Tweed to raise bitcoins. Hackers used some accounts for sale, and others sent private messages through their online networks to gain additional monetary support. Shivdeep (2020) goes into more details about this incident that maybe the attack on Twitter was carried out by company insiders. Similarly, in 2011, 6 million Chinese user profiles in the CSDN database were compromised, and user passwords were kept in plaintext. A number of collected personal data is stored in many large databases, and attackers can utilize the Internet to hack individual accounts. Commercial companies are reluctant to invest too much technology and money to effectively regulate their user data, eventually resulting in data misuse.
Some implementable measures
Preventing the misuse of private information is a hard task that governments or agencies, platform operators and individuals should make a concerted effort. Firstly, users should enhance the awareness of protecting their personal data and focus more on the platform’s terms of service. Personal rights to know and decide on information should also be protected in law. In 2020 October, Chinese government issued a draft of the Personal Information Protection Law, which clarified the principle of personal information processing with ‘consent & notification’ as the core. What’s more, the draft also divided personal data and put strict restrictions on the processing of sensitive information, which can be handled only when it is necessary for a specific purpose and with individual’s consent.
Secondly, the law should regulate the secondary use of personal data on platforms. In 2019, the French National Data Protection Commission (CNIL) found that Google’s contractual agreement structure undermines transparency, and lacks valid notification and user consent for personalised advertising (Valtysson, Jorgensen & Munkholm, 2021). Therefore, Google was fined EUR 50 million by CNIL because of violating of the EU’s General Data Protection Regulation (GDPR). If the user believes that the customized recommendation has a negative impact on his or her rights or just emotions, he or she can request the personal information processor to explain it, and has the right to refuse the processor to make automatic decisions only through data, algorithms, or AI.
Thirdly, everyone should have the right to request platforms to forget the personal information they all have. Doval & Pankaj in Indian white paper figure out that it’s quite common for users to regret revealing their personal information online. Unlike users, online platforms belonging to the Internet companies have almost absolute power over how they are operated (Suzor & Nicolas, 2019), and personal information on the internet is never really forgotten depending on powerful storage capabilities. According to Twitter’s contract documents, although the user account is deleted, the user’s data, including personal data, will be retained with unlimited time (Shivdeep, 2020). There should be choices for users to decide whether deleting their personal data from the internet “to remove the ‘shackles of unwise past things’ on the Internet and to correct past behaviours.”
Technical difficulty is another point for platforms needed to break through. Users want their posted personal data to remain secret for ever, but the situation is that the misuse of personal data is often accompanied by the leakage of personal privacy. Platforms should set up technical barriers to prevent hacker attacks and protect personal accounts and databases.
Conclusion
The problem of personal information misuse is becoming more and more serious, not only because platforms are pushing it for commercial benefits, but also because individuals or organizations have illegal purposes or use. The terms of service cannot become a legal means for the platform to misuse personal data randomly, and users should become the most direct informants, users and beneficiaries of their own personal information. Therefore, in the future, many relevant laws and regulations will be built and to defend the rights and interests of users.
Reference list
Brian X. Chen. (2019). I Shared My Phone Number. I Learned I Shouldn’t Have: Tech Fix. New York Times (Online).
Flew, T. (2014). New media (Fourth edition.). South Melbourne, Vic: Oxford University Press.
Hannah Murphy. (2020). Hackers stole personal data from Twitter accounts. FT.com.
Idjeri, A. (2018). Unfair Terms And Personal Data: Twitter Sentenced By A French Court. Mondaq Business Briefing.
Lupton, D., & Michael, M. (2017). “Depends on Who”s Got the Data’: Public Understandings of Personal Digital Dataveillance. Surveillance & Society, 15(2), 254–268. https://doi.org/10.24908/ss.v15i2.6332
Odusote, A. (2021). Data Misuse, Data Theft and Data Protection in Nigeria: A Call for a More Robust and More Effective Legislation. Beijing Law Review, 12(4), 1284–1298. https://doi.org/10.4236/blr.2021.124066
Pankaj Doval. (2017). Can individuals sue government, companies for personal data misuse, panel asks [Politics and Nation]. The Economic Times.
Pasquale, F. (2015). The black box society: the secret algorithms that control money and information. Cambridge: Harvard University Press.
Robinson, E. P., & Zhu, Y. (2020). Beyond “I Agree”: Users’ Understanding of Web Site Terms of Service. Social Media + Society, 6(1), 205630511989732–. https://doi.org/10.1177/2056305119897321
Shivdeep Dhaliwal. (2020). Benzinga: Twitter Hackers Downloaded Personal Data Of Some Of The Users, Company Says. In Newstex Finance & Accounting Blogs. Chatham: Newstex.
Some Twitter users’ personal data may have been breached. (2020). Mint (New Delhi, India).
Suzor, Nicolas P. 2019. ‘Who Makes the Rules?’. In Lawless: the secret rules that govern our lives. Cambridge, UK: Cambridge University Press. pp. 10-24.
Valtysson, B., Jorgensen, R. F., & Munkholm, J. L. (2021). Co-constitutive complexity: Unpacking Google’s privacy policy and terms of service post-GDPR. Nordicom Review, 42(1), 124–140. https://doi.org/10.2478/nor-2021-0033
Walrave, M., Vanwesenbeeck, I., & Heirman, W. 2012. Connecting and protecting? Comparing predictors of self-disclosure and privacy settings use between adolescents and adults. Cyberpsychology: Journal of Psychosocial Research on Cyberspace, 6(1), article 3.