

When one hears the word digital age, computers or the internet come into mind, and why not the internet has become a part of human life. As is the case with everything in this world, the digital world has its own pros and cons. Obviously, the digital world is alluring, captivating as well as inviting. Only a meagre fraction of people is unaware of this world, and as time passes by this fraction will go down drastically and finally become zero. If one of us simply chooses not to use the internet or related services of the digital world we would lose our identity and be socially isolated.
As the impact of this digital world is colossal on our daily lives, we cannot neglect its importance. With further technological advancements in this field, the concerns for digital fraud and privacy issues grow concurrently. To be honest, a lot of people don’t even think of this, and they are just concerned with the services they are availing and unaware of the cost that they are paying. There is also a subset of people who knows this potential issue but simply do not care because they think that their information is just not too important for someone to know and why on earth would anyone care to steal their information.
A survey conducted on the Australian population reveals “two general stereotypes: ‘I have nothing to hide’ and ‘Privacy concerns are exaggerated’” (Goggin et al., 2017, p. 14). This was notably true for people who are old or high school students but those under 40 seemed more concerned about their privacy (Goggin et al., 2017). Such stereotypic views can only be changed via awareness and education about privacy concerns.
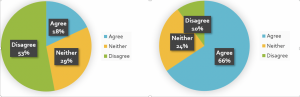
I have nothing to hide Concerns about privacy online are exaggerated
Undoubtedly, the privacy threats are alarming and critical. To put it simply, every bit of information that you put on the web is viable to be exploited. This information includes your personal details, credit cards, bank accounts, contacts, family, relatives & relationships, photos, videos, or anything that you may have put on the web. The threats to privacy are enormous with far-reaching consequences. There is no flawless way to shield your privacy, the best an individual can do is to minimize the risk. If you’re thinking of using VPNs or other apps to protect yourself, remember that you are trusting them too.
You probably have heard this famous quote from Gabriel García Márquez’s words, “All human beings have three lives: public, private, and secret.” All three have now been digitalized. The core issue of this digitalization is privacy. All of us know the meaning of the word privacy but ask yourself do I really understand the word or its importance. In a nutshell, privacy is “the right to be let alone” (Moore, 2003, p. 215). It gives an individual autonomy on certain matters that he wishes to disguise from the public. As the world has become a digital world and so does the concept of privacy.
The digital world has brought new challenges in the realm of privacy and user protection. With the development of Web 2.0 privacy has become a major concern. Social media sites such as Facebook, Twitter, TikTok, etc. have become a part and parcel of life and people are giving their personal details out on the internet via such sites. According to a survey conducted by the Pew Research Center on 1040 adults, “A majority of Americans (64%) have personally experienced a major data breach, and relatively large shares of the public lack trust in key institutions – especially the federal government and social media sites – to protect their personal information” (Smith, 2017, para.15). A large fraction of people provides their true details on social media sites and leave digital imprints such as cookies while they are surfing through the website. A study done at Carnegie Mellon University in 2005 analyzed 4540 Facebook profiles, they examined the name quality of 100 profile names and found that 89% used real names while 3% used partial names and 8% used fake names (Gross et al., 2005). Many users also don’t bother to review the privacy controls they have.
Thus, users are giving too much of their information without considering its potential consequences. All these social media sites share user information with advertising companies. For instance, if a user on Facebook clicks on an ad or uses a third-party app, Facebook would send user information to third parties.
.
Another thing that is quite popular nowadays is location. Websites like search engines or applications like WhatsApp, Facebook, etc. can collect user’s location information without letting the user know. Also, people tend to share their location often on Facebook like where they are right now and where they might be headed. Smartphones are also facilitating location tracking. This could lead to various types of crimes.
Online harassment is also intimately related to privacy. This is also referred to as cyberbullying. Hate speech, body shaming, mean posts, and comments about a particular personality, community, society, country, or organization can promote negativity among people about that person or community or country. Racism also comes under this realm. It can be called as “platformed racism” (Matamoros-Fernández, 2017, p. 931). Adam Goodes’ controversy is worth mentioning in this regard. The ill policies of social media sites like Facebook, and Twitter paved the way for such an awful event.
“Before reading this blog, please verify that you are a human,” all of us have seen such messages where you solve a puzzle or a captcha in order to proceed further on that site. A Bot is not a real user, but technically a computer navigating the site as a user. Bots have been utilized negatively in Politics as seen in 2016 U.S elections, where Hillary Clinton and Donald Trump both used bots to attract more votes. Bots can also be used to alter people’s views about a certain belief, religion, or community by spreading hate speech, false news, and lies over social media. Although websites are developing a counter mechanism to avoid bot traffic on their sites, but the countermeasures are strengthening as well. One can literally buy software online that can create say for example 500 Gmail accounts, software will behave like a real human being and fill in all the detail with pre-fed information. Besides, different websites also sell Facebook, Gmail, Twitter, and Apple ids, and all that one needs to do is pay.
 Besides, the internet also offers its users to inquire about others in ways that may affect others’ privacy. Assessment of one’s Facebook profile, Twitter profile, or browsing history or logs can reveal a lot about one’s beliefs, views, hobbies, or interests. Also, there are many online services as well where you can pay to investigate a certain piece of information like finding out the name or other details using a phone number. This has been made possible because people put their contact details on the internet and these websites collect such information to make a directory that contains all the details.
Besides, the internet also offers its users to inquire about others in ways that may affect others’ privacy. Assessment of one’s Facebook profile, Twitter profile, or browsing history or logs can reveal a lot about one’s beliefs, views, hobbies, or interests. Also, there are many online services as well where you can pay to investigate a certain piece of information like finding out the name or other details using a phone number. This has been made possible because people put their contact details on the internet and these websites collect such information to make a directory that contains all the details.
In this era of the digital age, an enormous amount of digital data is being generated which resultantly increases the risk of a data breach. With the development of E-commerce, people like to buy goods online using credit or debit cards, with every transaction their information is being monitored and recorded. This information is stored in databases, leakage of this information can occur, and such a data breach would lead to a financial loss on the side of the consumer. People also tend to share their sensitive details like pins, passwords, etc. on various apps like WhatsApp, Facebook messenger, and others without realizing the fact that their credentials could be stolen. The most popular among these is WhatsApp. In December 2019, WhatsApp confirmed a bug in the application that allowed hackers to access a user’s data (Valinsky, 2019). The hackers would send a malicious GIF file to a user, and when the user viewed gallery within the app, hackers could access the recipient’s data. There have been other kinds of data breaches as well. There are also some modified versions of WhatsApp available on the web, these versions have certain features that are not available to ordinary users such as the ability to see deleted messages or to see when the last online status of that individual. It is due to such reasons that countries like the UAE, China, North Korea, and Qatar have banned WhatsApp.
“Please accept our cookies,” a message we get many times while surfing the web. A cookie in the simplest sense is a tracker but not a simple tracker that one would have in his or her car that reads the driver’s locations. For obvious reasons the websites don’t like to use the word tracker, so they choose the fancy word ‘cookie’. Cookies can record all sorts of information like your device information, location, purchases, search history, ads, and links that you may have clicked. Via cookies, it is also possible to find out what pages the user visited and for how long did he stayed there. Guess what, all of this and much more is collected without you knowing.
As the world is becoming more digital than ever before, the use of AI or artificial intelligence has become common. People now use AI devices in homes and offices. Such devices include cameras, Alexa or Google Home, sensors, etc. These devices carry a lot of information like whether the individual is at home or not and footage as well. There have been incidences where hackers gained access to security cameras and could see people in their homes. Researchers have also demonstrated how Amazon Echo could be used as a spying device that could record people’s conversations (Lily Hay Newman, 2018).
Although some of the major threats are discussed in this blog, there is an inexhaustive list of threats that needs to be addressed. As time passes by, we would reach a state where it would be impossible to separate the physical from the digital. The privacy threats are mounting day by day and organizations should take effective steps to control the situation. In the US, the FTC (Federal Trade Commission) provides the public with the legal right to privacy. Section 5 of the FTC Act protects consumer privacy whenever a company attempts to collect or retrieve personal information in a rather deceiving or unfair manner (A. Valentine, 2000). Attempts have been made to protect user privacy in various ways. If you are a WhatsApp user you probably would have heard the word encryption, which simply means to convert information into codes or a language that could not be understood by anyone. It is not a new concept; humans have been utilizing these methods for years. But since the emergence of the digital world, our methods of encryption have also been digitalized. The End-to-end encryption introduced by WhatsApp is an important protective measure in this regard. End-to-end encryption means that the information being sent or received on WhatsApp is encrypted or decrypted on the user’s device only and no one even WhatsApp can view the content of the messages.
Another way to stay safe on the web is the use of VPNs (Virtual Private Networks), which channels the user’s data traffic through an encrypted tunnel. Giving users the power to restrict the data accessing ability of an application can also improve user privacy i.e., users can allow themselves whether an app can access the phone gallery or not or only access the gallery once or for a particular period. Efforts could also be done to limit the amount of information the user needs to provide while availing a particular service. Additionally, the use of antiviruses can also protect users’ privacy and keep them safe from attacks by hackers.
The privacy concerns should be addressed because it is a global issue. Considering that privacy threats are much more potent than countermeasures, we should look out for more ways to improve our current situation. Since privacy is in our DNA, we should be constantly on the hunt to find new ways to protect user privacy and data.
———————————————————————————————————————————————————
References
- Valentine, D. (2000, February 11). Privacy on the Internet: The Evolving Legal Landscape. Federal Trade Commission. https://www.ftc.gov/news-events/news/speeches/privacy-internet-evolving-legal-landscape
Goggin, G., Vromen, A., Weatherall, K. G., Martin, F., Webb, A., Sunman, L., & Bailo, F. (2017). Digital rights in Australia. Digital Rights in Australia (2017) ISBN-13, 978-0.
Gross, R., & Acquisti, A. H. John Heinz, I. 2005. Information revelation and privacy in online social networks. In WPES’05: Proceedings of the 2005 ACM Workshop on Privacy in the Electronic Society (pp. 71-80).
Matamoros-Fernández, A. (2017). Platformed racism: The mediation and circulation of an Australian race-based controversy on Twitter, Facebook and YouTube. Information, Communication & Society, 20(6), 930-946.
Moore, A. D. (2003). Privacy: its meaning and value. American Philosophical Quarterly, 40(3), 215-227.
Newman, L. H. (2018). Turning an Echo Into a Spy Device Only Took Some Clever Coding. Wired.
Smith, A. (2017, January 26). Americans and Cybersecurity. Pew Research Center: Internet, Science & Tech; Pew Research Center: Internet, Science & Tech. https://www.pewresearch.org/internet/2017/01/26/americans-and-cybersecurity/
Valinsky, J. (2019, October 7). WhatsApp had a bug that let hackers take over phones with a GIF. CNN. https://edition.cnn.com/2019/10/07/tech/whatsapp-gif-bug-trnd/index.html