
After the advent of the internet for consumers in the 1990s, companies’ data collection efforts increased exponentially and haven’t slowed down over the past couple of decades, especially later the social media popularized. As the report of Digital right Australian (2017) said, a minority (38%) feel they can control their privacy online. With the increasing data that is generated about us, customer beginning to concern the issue of personal data misusing. For example, some users noticed when we are talking about the product we want to buy, the ad of it will immediately appeared online. According to the Internet Society and Consumers International (2020), 69% of consumers are worried about how their personal data is collected in mobile apps. That’s a far cry from the 0.01% who opted out of the Lotus database (Fobe,2020)
In terms of this issue, social media platforms definitely attract the most focus, 2019 being notorious for cyberattacks and data breaches. Social media, especially amongst influencers has been about “sharing” and this includes over sharing, often of personal information. A large majority (78%) want to know what social media companies do with their personal data. (Australia Digital right,2017)
However, people gradually found not only social media relate directly to privacy issue. Back in 2016, before face book’s Cambridge Analytica data privacy debacle, some customers found that startup also has privacy issue. Consumers were not aware of the amount of information companies were collecting previously (before 2015). As consumers become more aware of how businesses use their data, privacy concerns have risen. More and more information breaches in companies destroyed the trust between platform and users, the misuse of data result in infliction) of harm to another person (harm to good name and reputation or violation of privacy for example profile photo is accessed and used in illegal way) and result in the devastating economic losses. Next, this blog will take twitter (social media) as example to explain the threat and consequence of privacy data misuse, then focus on the data leakage of startups. Finally, we will deeply analysis the causes of this situation and wish this blog could protect you from leakage accident.
Threats and Consequences
More and more misuse of privacy information destroys the trust between platforms and users. Correctly using the privacy data could protect user’s property and personal safety. Certain US companies, such as Facebook, continue to exploit data with little constraints on third-party usage and monetisation (NBC News 2018). They are weakening confidence and jeopardizing privacy as well as democratic discourse in the process (The Guardian 2019). Foreign corporations with ties to governments can potentially profit from a lack of personal data governance. They can make enticing applications that watch users, such as ToTok (The New York Times 2019b), or they can disclose data without intent, as in the case of the worldwide Strava heatmap (Wired 2018). These companies might potentially use these data to attack other countries or citizens by combining it with other databases. There are growing fears that the applications Grindr and Tiktok, if placed in the wrong hands, may be misused.

Image from: The daily Swing
Twitter acknowledged in September 2019 to allowing marketers access to its users’ personal data in order to better the targeting of marketing efforts. The problem, which the firm described as an internal oversight, was that Twitter gave Twitter’s Tailored Audiences marketers access to user email addresses and phone numbers. Without our approval, Twitter’s ad purchasers might cross-reference their marketing database with Twitter’s to discover shared consumers and deliver them customized advertising. What even worse once the privacy data leak, social engineering scammers could use cloned social media accounts to carry out deceit. Twitter bots are being used by fraudsters to deceive unwary tweeters into making PayPal and Venmo payments to accounts under their control. The bots appear to be launched when a real user asks another for payment information, probably after searching for terms like ‘PayPal,’ ‘Venmo,’ or other services. They impersonate the other user by the leaked profile image and using a similar username, then providing them with bogus payment details in the hopes that the original tweeter would pay into this account.
Startups also have privacy issue
In the wake of the advancement of E-Commerce, many business startups emerged, such as Tokopedia, Gojek, Traveloka, and Bukalapak, which are growing along with technology. Consumers must first register themselves by filling in their personal information, such as their full name, place and date of birth, telephone number, address, and others before they can use the application. In this case, each startup has personal data about us as consumers. Users therefore, are unable to use ecommerce sites without handing over their personal information. Each startup offers its advantages by providing transactional convenience. However, the advantages offered by these start-ups do not exclude the possibility of problems. One of the serious issues lies in maintaining the privacy of the consumers of the start-ups. The potential for these issues to arise needs to be considered in terms of ensuring security and privacy transactions, i.e. protecting consumers’ personal data, which could lead to problems in the future if a data breach occurs. Based on the above, it can be said that the emergence of startups is like two sides of the same sword; on the one hand, it facilitates transactions. On the other hand, there is the possibility of misuse of the personal data of the startup consumers.
Tokopedia

The image from Jakarta Post
In 2020 May 1, a hacker has leaked the details of 91 million users registered on Tokopedia, Indonesia’s largest online store, which all of these information was selling in the dark web marketplace as 5000$. ZDNet has obtained a copy of the leaked file with the help of data breach monitoring service Under the Breach. The file contained a PostgreSQL database dump comprising user information such as complete names, email addresses, phone numbers, hashed passwords, dates of birth, and Tokopedia profile information (account creation date, last login, email activation codes, password reset codes, location details, messenger IDs, hobbies, education, about-me fields, and lots more). ZDNet has verified the authenticity of the leaked data against the official Tokopedia website.
Image: leakage evidence document from ZDNet
This accident mirror that having a big number of workers with access to the company’s internal systems put huge enterprises like Tokopedia at a disadvantage. Hackers frequently utilize social engineering strategies to send phishing emails to workers, which in turn grants them access to various systems within the firm. Furthermore, large corporations typically rely extensively on third-party firms’ products that link with their systems, which means the third parties have access to the company’s internal and sensitive networks, increasing the danger of hacking. Besides, according to the survey (ZDNet, 2020), these e-commerce sites just keep personal data in plaintext format, without encryption, they even display bare personal data without any packaging or protection in the database. Compared to account password, personal data will sell far more. The password could be change, especially after the leakage incident. However, the personal information like cell phone, e-mail, full name/address cannot be changed.
Causes of privacy data misuse
Given the recent history of high-profile consumer-data breaches, customers lack confidence to the companies, but it is reasonable. However, causes of these terrible accidents definitely not simple, it related to various aspects for example company management, government involving even the personal causes.
- Companies’ slack management
“Unfortunately, although [the data leak] happened a few days ago, there has still not been any written notification from the Tokopedia platform provider to its consumers as personal data owners,” (Eisya A,2020)
It is no doubt that company management is the most important. Mckinsey (2020)reported that about half of the consumers polled indicated they are more inclined to trust a firm that requests just information related to its products or restricts the quantity of personal data sought. These indicators appear to indicate to customers that a corporation is concerned about data management. In addition, nearly 50% of user respondents are more likely to trust businesses that respond fast to hacks and breaches and publicly expose such instances to the public. As the impact of data breaches rises and more restrictions limit the timing for data-breach reports, these practices have become increasingly crucial for both businesses and consumers.
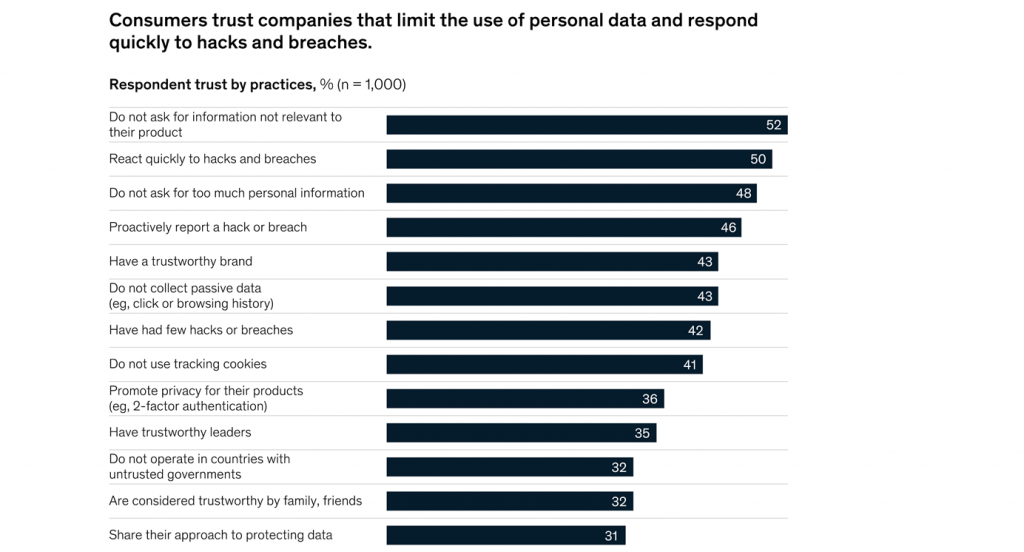
Image from Mckinsey 2020 survey: The consumer-data opportunity and the privacy imperative
- Consumers’ attitude and action
“Although people say they care very much about privacy, they behave as if they did not” (Francis and Francis, 2017, p. 46)
For example, after the leakage accident of Twitter, it did not appear to suffer much from the scandal — in its first quarterly earnings report since the story broke, the company reported that daily active users were stable, and revenue increased 49 percent year over year.
When face the tedious conditions and the lines around “consent” becoming increasingly blurred, will you annoyed and just click “Agree all”? What the most concerning is that people have get use to filled lots of information when they are shopping online or accessing some websites, and forgot they have authority to say no especially the General Z, Millennium who are the technical-savy, growing up in the technique’s environment. Thus, the privacy right should be popularized, which improve the user’s awareness concerning the spreading and managing of networks data.
- Loophole in legal regulation
Deliberations on Indonesia’s version of the European Union’s General Data Protection Regulation (GDPR) have stagnated since the administration submitted a draft law to the House of Representatives in January.(The Jakarta Post,2020)
GDPR is a respectively excellent legal system in the world, however according its requirements, personal data should be encrypted throughout data exchange and storage in Europe. But Encryption is not required. The phrase “encryption” comes just four times in the 260 GDPR pages, and they are all suggestions (pages 51, 121, 160 and 163). Encrypted data is not regarded as personal data under the GDPR. That is, if the leaked data is encrypted data so that it cannot be used to identify individuals, violations of the data leakage are not as severe if without encryption. Besides, not each country has their own local excellent legal system to protect the privacy information. Not only Indonesia, compared to the GDPR, Australia’s legislators have been hesitant to react (Daly, 2017). Australian privacy law is a combination of statute and common law. There is no right to privacy established in the Constitution, and, unlike many other liberal democracies, Australia lacks a Commonwealth-wide constitutional or statutory Bill of Rights. The collecting and processing of information by the government and bigger private sector actors is controlled by the Privacy Act 1988 and a variety of state and territory laws. This does not provide an enforceable right to privacy.
Conclusion
Often, data misuse is the result of ignorance and neglect. However, as our digital footprints increase and adapt, the need for good onlinhabit applies to all internet users, not just IT professionals. Mixing professional and personal devices is not a good idea. Never download business data to your own laptop, smartphone, desktop, home server, or whatever device you like, regardless of how sophisticated your home firewall, encryption, or VPN is. This confluence of events simply attracts more scrutiny and more potential for cyber-attacks. Confirm URLs before providing personal information, avoid clicking links from unknown email addresses, and use complex passwords. While we may fine-tune and improve our internet behaviors to avoid possible misuse, we seldom have the opportunity to define data rules for the businesses we visit. As consumers, customers, and contributors, we must hold the companies we rely on accountable for meeting those expectations. Instead of imposing a high penalty, authorities could strengthen the degree of monitoring to promote customer trust, which would successfully increase e-commerce platform revenues while also protecting consumers’ privacy. Organizations should have fundamental security structures in place, such as behavior alerts and access control tools, which should be supplemented with need-to-know access and zero-trust designs. Similarly, as consumers, we have a right to understand data collecting practices and use cases. In this Blog we have not discuss deeply in legal field, however, as governing legislation such as the EU’s GDPR and California’s CCPA continue to determine the future of data regulation, it is only a matter of time until global norms about data ownership and abuse become more apparent in every country.
Reference:
Becker, M. Privacy in the digital age: comparing and contrasting individual versus social approaches towards privacy, Ethics Inf Technol 21, December 2019, pp. 307–317 <https://doi.org/10.1007/s10676-019-09508-z>
Dian F, A Tulus S, Fitriati, The Urgency of the Personal Data Protection Law as an
Instrument to Prevent Misuse of Personal Data in StartUp Companies, International Journal of Social Science And Human Research, December 2021, vol.04, pp.3603-3605
Goggin, G., Vromen, A., Weatherall, K., Martin, F., Webb, A., Sunman, L., Bailo, F, Digital Rights in Australia, 2017, The University of Sydney.
Jessica Haworth, Social media scam: Twitter bots are tricking users into making PayPal and Venmo payments into fraudsters’ accounts, 28 September 2021, portswigger, view at 1st April 2022, <https://portswigger.net/daily-swig/social-media-scam-twitter-bots-are-tricking-users-into-making-paypal-and-venmo-payments-into-fraudsters-accounts>
Swish Goswami, The Rising Concern Around Consumer Data And Privacy, Forbes, December 2020, viewed at 30th March 2022, <https://www.forbes.com/sites/forbestechcouncil/2020/12/14/the-rising-concern-around-consumer-data-and-privacy/?sh=6b54fe13487e>
Venky A, Lisa D, James K, Henning S, The consumer-data opportunity and the privacy imperative, April 27, 2020, Mckinsey, view at 30 May 2022, <https://www.mckinsey.com/business-functions/risk-and-resilience/our-insights/the-consumer-data-opportunity-and-the-privacy-imperative>
Zuhri mahrus, Tokopedia, Bukalapak, and Bhinneka Leaks Data: Who Cares?, cyberthreat, 4 May 2020, viewed at 28th March 2022, https://cyberthreat.id/en/read/42/Tokopedia-Bukalapak-and-Bhinneka-Leaks-Data-Who-Cares#